- word
- Pre Security
- Introduction to Cyber Security
- Offensive Security Introduction
- gobuster
- Defensive Security Intro
- Security Operations Center (SOC)
- Digital Forensics and Incident Response (DFIR)
- Digital Forensics 数字取证
- Incident Response 事件响应
- Malware Analysis 恶意软件分析
- Offensive Security Introduction
- Introduction to Cyber Security
word
| 单词 | 意思 |
|---|---|
| simulated | 模拟 |
| complement | 补充 |
| portal | 门户 |
| ethical | 有道德的 |
| leveraging insecure setups | 利用不安全的设置 |
| penetration testers | 渗透人员 |
| Vulnerabilities | 漏洞 |
| remediate | 补救、矫正 |
| violation | 违反、违抗 |
| Policy violations | 策略违规 |
| confidential | 机密的 |
| Network intrusions | 网络入侵 |
| malicious | 恶意的 |
| threat intelligence | 威胁情报 |
| adversely | 不利的、有害的、反而 |
| adversary | 对手 |
| halt | 停止、犹豫 |
| petroleum refinery | 石炼油厂 |
| ransomware | 勒索软件 |
| forum | 论坛 |
| phase | 阶段 |
| a format suitable for analysis | 适合分析的格式 |
| tactic | 战术、战略 |
| consequently | 因此、结果 |
| investigate | 侦察 |
| evolved into | 演化为 |
| cyber espionage | 网络间谍 |
| traverse | 遍历 |
| entail | 牵涉、需要 |
| breach | 破坏、破裂、违约 |
| data breach | 数据泄露 |
| misconfiguration | 配置错误 |
| containment | 抑制、遏制 |
| eradication | 根除、消灭 |
| underneath | 在····下方 |
| shady | 隐蔽的、可疑的、背阴的 |
| Scenario | 方案、场景、剧本 |
| dashboard | 仪表盘 |
| expertise | 专长技能 |
Pre Security
Introduction to Cyber Security
Offensive Security Introduction
To outsmart a hacker, you need to think like one.
Penetration Tester - Responsible for testing technology products for finding exploitable security vulnerabilities.Red Teamer - Plays the role of an adversary, attacking an organization and providing feedback from an enemy's perspective.Security Engineer - Design, monitor, and maintain security controls, networks, and systems to help prevent cyberattacks.
gobuster
一个爆破工具
gobuster -u http://fakebank -w wordlist.txt dir
-u表示网站 -w表示对应爆破词表
Defensive Security Intro
Security Operations Center (SOC)
A Security Operations Center (SOC) is a team of cyber security professionals that monitors the network and its systems to detect malicious cyber security events
Digital Forensics and Incident Response (DFIR)
Digital Forensics 数字取证
In defensive security, the focus of digital forensics shifts to analyzing evidence of an attack and its perpetrators and other areas such as intellectual property theft, cyber espionage, and possession of unauthorized content.
File System、System memory、System logs、Network logs
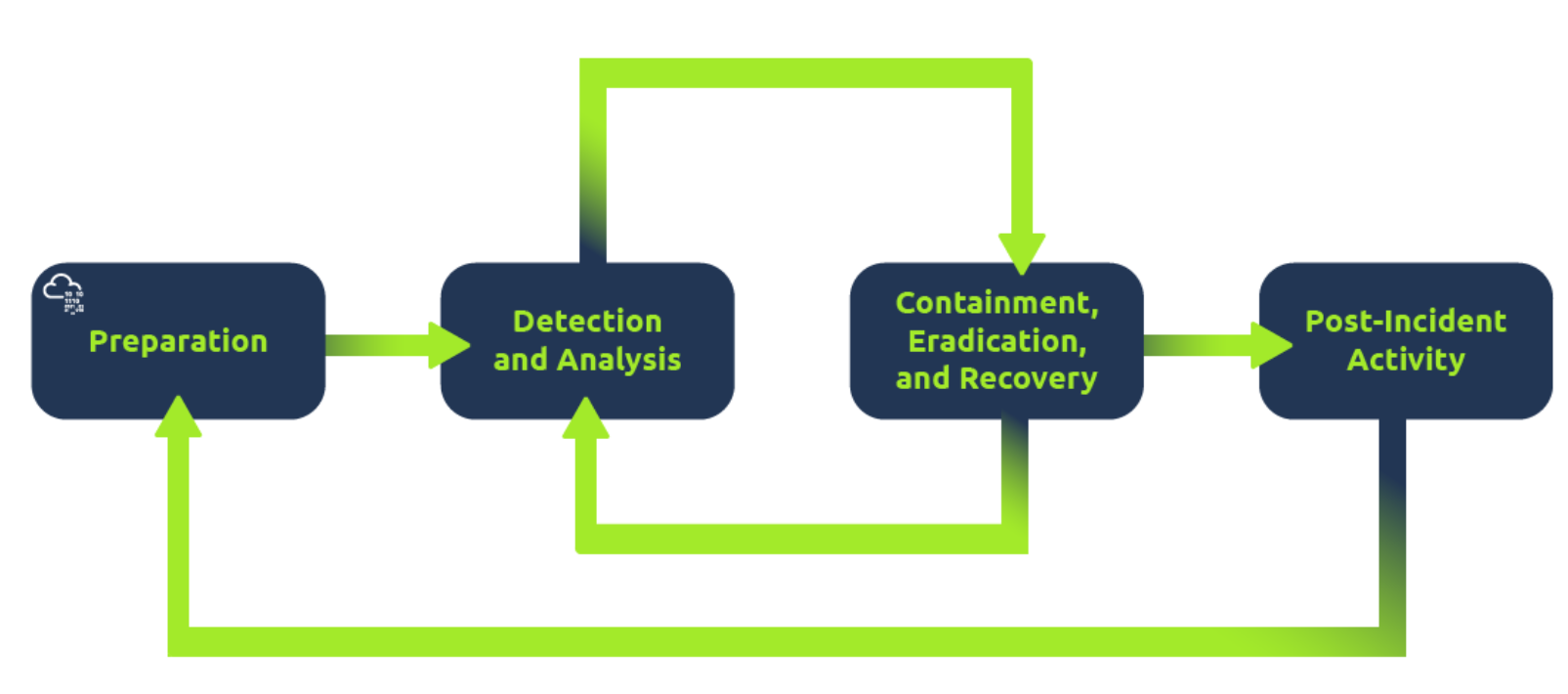
Incident Response 事件响应
Incident response specifies the methodology that should be followed to handle such a case. The aim is to reduce damage and recover in the shortest time possible.
Malware Analysis 恶意软件分析
AbuseIPDB 和 Cisco Talos Intelligence可以用来进行ip分析
