Tags:流量分析,文件分离,pyshark,SQL注入,正则匹配
0x00. 题目
附件路径:https://pan.baidu.com/s/1GyH7kitkMYywGC9YJeQLJA?pwd=Zmxh#list/path=/CTF附件
附件名称:20250626_黔西南网信杯_wireshark.zip
0x01. WP
1. 解压附件,FOREMOST分离出流量附件
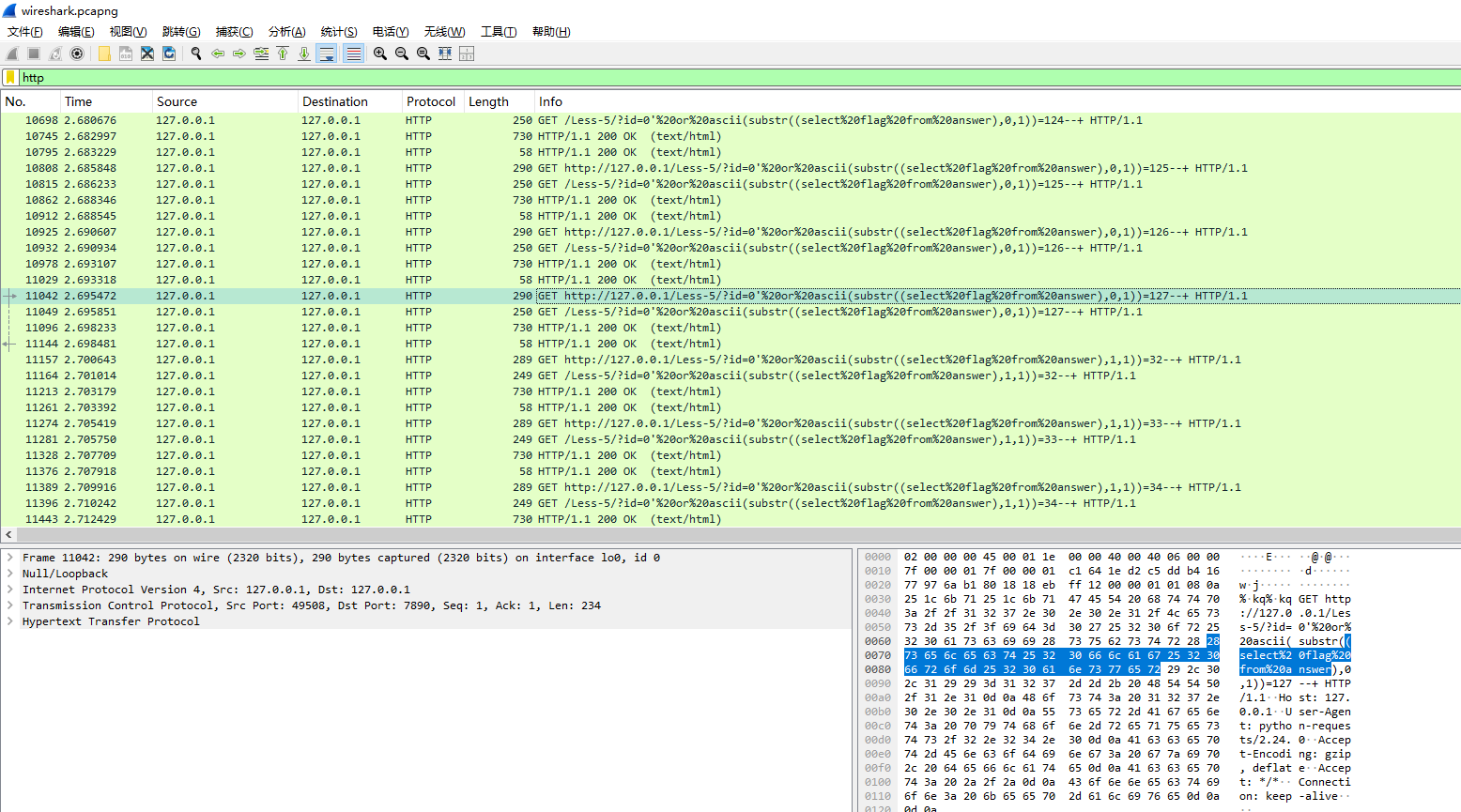
2. 浏览流量包http请求
发现为常规SQL注入的GET请求,直接对目标字段逐位进行爆破
3. 使用通用协议解析代码,利用正则匹配进行数据提取
分析爆破数据,发现爆破成功后http.data字节长度为704,并包含You are in关键词
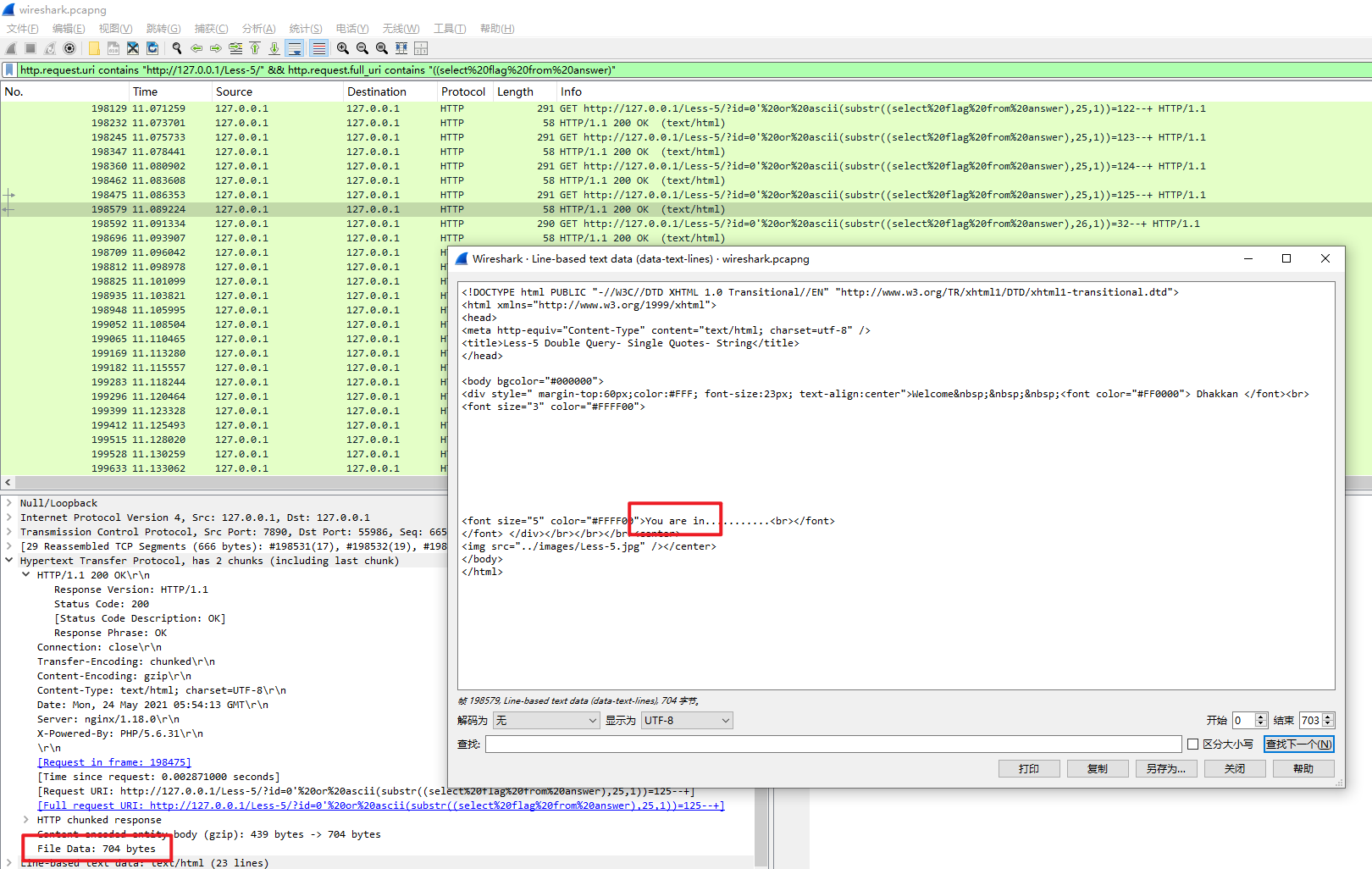
整理过滤表达式提取爆破成功的响应包数据:http.request.uri contains "http://127.0.0.1/Less-5/" && http.request.full_uri contains "((select%20flag%20from%20answer)" && http.file_data contains "You are in"

exp.py
# -*- coding: utf-8 -*-
import pyshark, os, re,time# Author: Jason.J.Hu
# Create : 2023/12/11# 初始化全局参数
strCapPath = "wireshark.pcapng"
strTsharkPath = "D:\\=Green=\\Wireshark\\App\\Wireshark\\"strFomula='http.request.uri contains "http://127.0.0.1/Less-5/"'
strFomula+=' && http.request.full_uri contains "((select%20flag%20from%20answer)"'
strFomula+=' && http.file_data contains "You are in"'
tFlag=""cap = pyshark.FileCapture(strCapPath, display_filter=strFomula,tshark_path=strTsharkPath)print(time.strftime("%H:%M:%S", time.localtime()), "HTTP分析开始 ... ...")# 协议结构分析开始
print("协议结构分析开始...")
i=0
for layer in cap[0].layers:print("第",i+1,"层:",layer.layer_name)print(layer.field_names)i+=1
print("协议结构分析完成。")
print("=" * 16)lstResult=['','','','']
sFlag=""
for pkt in cap:intRequestNumber = pkt.numberprint("\r\tFrame Number: %s ..." % str(intRequestNumber), end="")sRequestURI=pkt.http.request_uri# print(sRequestURI)# http://127.0.0.1/Less-5/?id=0'%20or%20ascii(substr((select%20flag%20from%20answer),3,1))=71--+lstRE=re.search(r'''select%20flag%20from%20answer\),(.*?),1\)\)=(.*?)--+''', sRequestURI)print(lstRE[1],lstRE[2])if len(lstResult)<(int(lstRE[1])+1):lstResult.append("")lstResult[int(lstRE[1])]=chr(int(lstRE[2]))# print(lstResult)print("\r")
sFlag="".join(lstResult)
print(sFlag)
print("\r")
print(time.strftime("%H:%M:%S", time.localtime()), "HTTP分析结束。")# flag{W1re_Sha4k_and_SQLi}

 流量分析, 文件分离, pyshark, SQL注入, 正则匹配
流量分析, 文件分离, pyshark, SQL注入, 正则匹配