目录
- 找一个目标url 下一个xhr断点
- 换个思路查看一下网站资源
- 加密参数分析
- a0_0x5ae5d7['0'] 值分析
- a0_0x42e81e['8'] 值分析
- a0_0x42e81e['9'] 值分析
- a0_0x42e81e['10'] 值分析
- a0_0x42e81e['2'] 值分析
- a0_0x42e81e['3'] 值分析
- a0_0x42e81e['4'] 值分析
- a0_0x42e81e['11'] 值分析
- a0_0x42e81e['12'] 值分析
- 算法还原
找一个目标url 下一个xhr断点


# 跟了一下堆栈,没有找到相关逻辑
换个思路查看一下网站资源

# hxk_fec js文件很可疑 复制到解释器看看

# 有一个加密函数有点可疑,下个断点看看
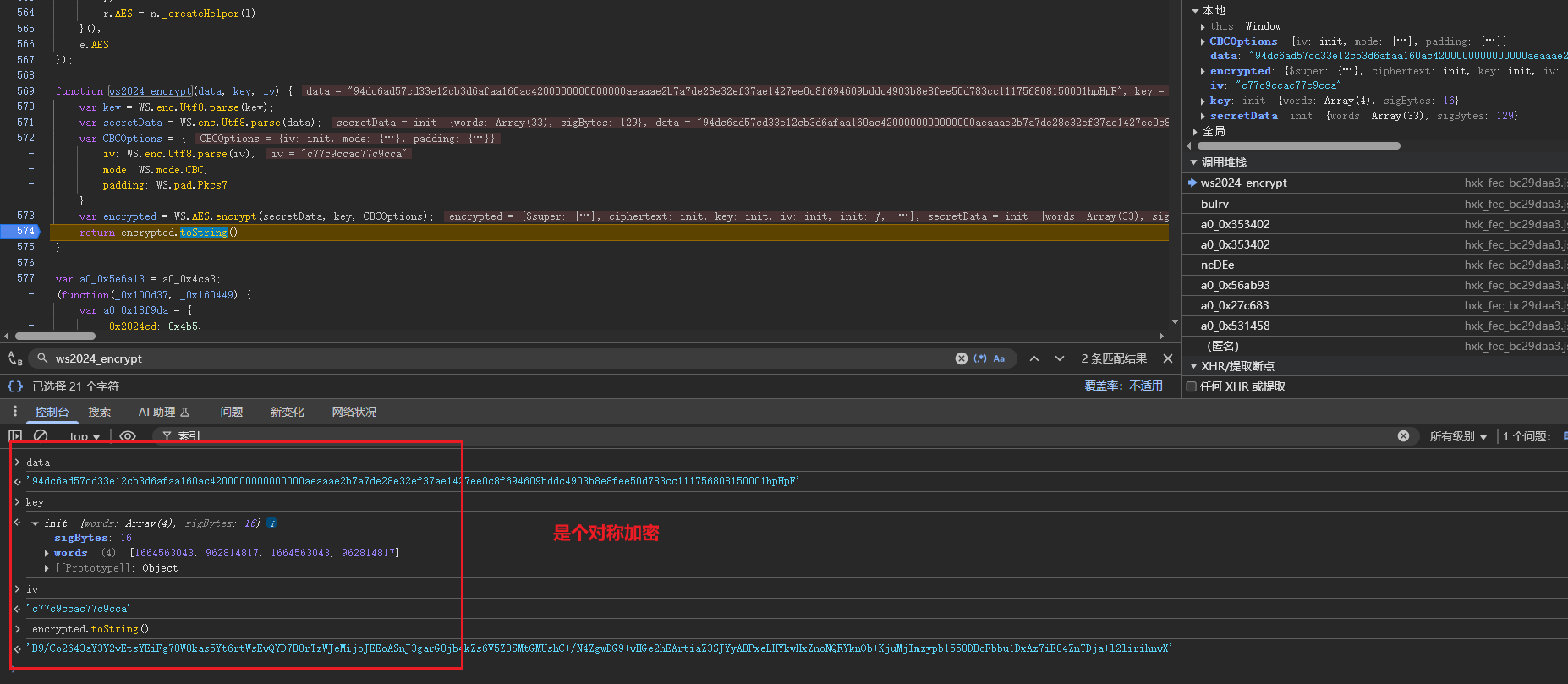
# 跟一下断点


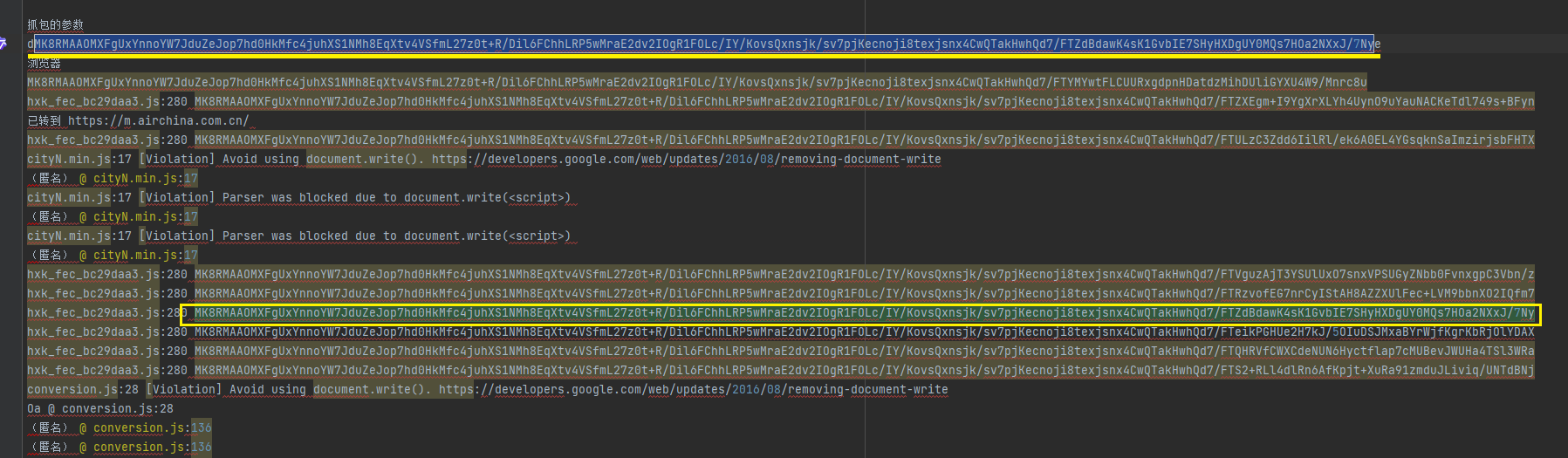
# 就是这个算法生成的加密值 头部和尾部加了额外的字符
加密参数分析



a0_0x5ae5d7 = {}
a0_0x5ae5d7['0'] = '',
a0_0x5ae5d7['2'] = '',
a0_0x5ae5d7['3'] = '',
a0_0x5ae5d7['4'] = '',
a0_0x5ae5d7['5'] = 0x0,
a0_0x5ae5d7['6'] = 0x0,
a0_0x5ae5d7['7'] = 0x0,
a0_0x5ae5d7['8'] = '',
a0_0x5ae5d7['9'] = '',
a0_0x5ae5d7['10'] = 0x6,
a0_0x5ae5d7['11'] = null,
a0_0x5ae5d7['12'] = '';
var a0_0x42e81e = a0_0x5ae5d7
// 简化一下
var a0_0x42e81e = {0: '', 2: '', 3: '', 4: '', 5: 0, 6: 0, 7: 0, 8: '', 9: '', 10: 6, 11: null, 12: ''}

a0_0x5ae5d7['0'] 值分析
// a0_0x5ae5d7['0'] 一个字符串的md5哈希值
a0_0x5ae5d7['0'] = ws2024_hex_md5(_0x4dbd78); -> "bf0d72ce84dbd68005d46feed3ef6f61"
_0x4dbd78 = "c1d0b6ffadc22fdaf8f2332e5827ecad0edfb7e62b955f1670ece6c06cddc2559f89e40316e4e062adf473bc5cf4396689fff75c719f1bb95efb798f6c5514380e9f532ac49f48c06a5bfc5d1f76bd79c7"// a0_0x4c64bc() -> 返回的字符串进行的md5

// 分析发现是 服务端响应的cookie
HTTP/1.1 200
Date: Mon, 08 Sep 2025 06:21:08 GMT
Content-Type: text/html;charset=UTF-8
Connection: keep-alive
Server: wswaf
Content-Language: zh-CN
Cache-Control: no-store
x-via: 1.1 PS-JJN-017ah155:2 (Cdn Cache Server V2.0), 1.1 PS-CGD-012yM35:4 (Cdn Cache Server V2.0)
x-ws-request-id: 68be75d3_PS-CGD-012yM35_27180-11016
Set-Cookie: HMF_CI=3cb773eb37e54e529340798f29b2d66bbcac709ffe1d380d9d845247753f8e362bf64d818faff3b6059abd29b8808f07c2341e80f382785c3f522d9f0608487303; Expires=Wed, 08-Oct-25 06:21:08 GMT; Path=/
Set-Cookie: FECW=c1d0b6ffadc22fdaf8f2332e5827ecad0edfb7e62b955f1670ece6c06cddc2556d56f8be4996fe36b6dfd895a88320d028dd960021eae1463ed630e311a06706c97532c4fd26f3bfadadd0b9a9da5d3f57; Expires=Thu, 06-Sep-35 06:21:08 GMT; Path=/; Secure
Vary: Accept-EncodingFECW 就是
a0_0x42e81e['8'] 值分析
'"none"' 做了一系列哈希得到的值

a0_0x42e81e['9'] 值分析
user-agent md5的哈希值
a0_0x42e81e['9'] = ws2024_hex_md5(_0x1a4d87);ws2024_hex_md5("Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36") -> "8f694609bddc4903b8e8fee50d783cc1"
a0_0x42e81e['10'] 值分析
["chrome","safari"
] 浏览器配置信息 直接写死
a0_0x42e81e['2'] 值分析
{"webdriver": "","auto_tool": ""
} 直接写死,一些检测
a0_0x42e81e['3'] 值分析
![] false 直接写死
a0_0x42e81e['4'] 值分析
"None" 先写死,后续分析
a0_0x42e81e['11'] 值分析
1757312528565 时间戳
a0_0x42e81e['12'] 值分析
SDq4d 随机值
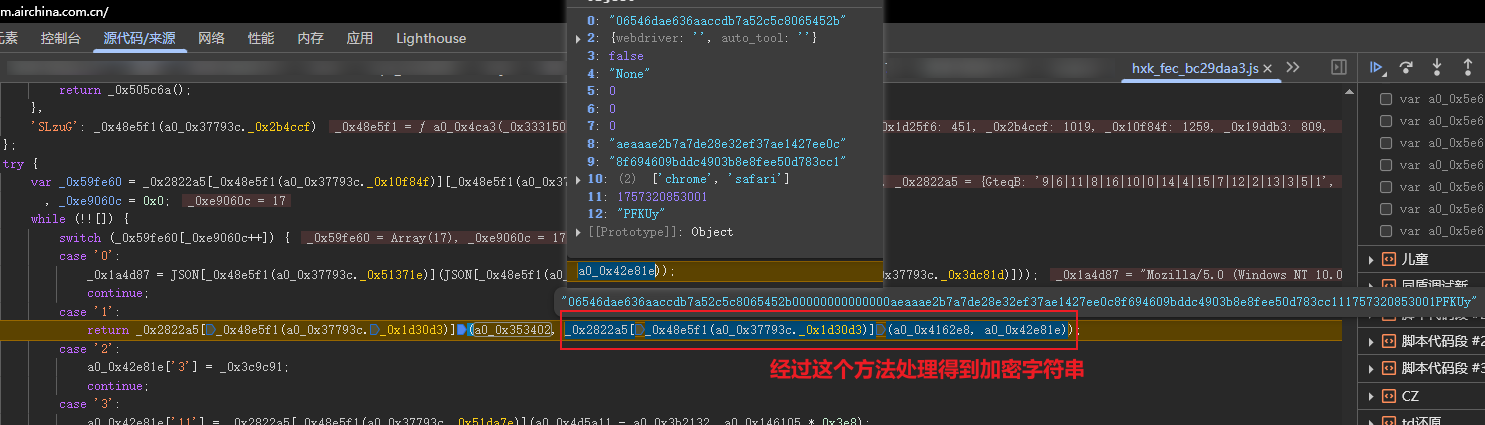
06546dae636aaccdb7a52c5c8065452b
00000000000000 // 14个0是一些函数返回值 直接写死
f6d62a8e69201d3806ac1ef24ec64c4d
8f694609bddc4903b8e8fee50d783cc1
11757315687001
wOoHt

算法还原
function ws2024_encrypt(data, key, iv) {var key = WS.enc.Utf8.parse(key);var secretData = WS.enc.Utf8.parse(data);var CBCOptions = {iv: WS.enc.Utf8.parse(iv),mode: WS.mode.CBC,padding: WS.pad.Pkcs7}var encrypted = WS.AES.encrypt(secretData, key, CBCOptions);return encrypted.toString()
}data
"06546dae636aaccdb7a52c5c8065452b00000000000000aeaaae2b7a7de28e32ef37ae1427ee0c8f694609bddc4903b8e8fee50d783cc111757322879598F2STU"
key
'c77c9ccac77c9cca'
iv
'c77c9ccac77c9cca'
encrypted.toString()
's6liFzJm+Czk7nfJHm/Ml7+A7Kvp+Wd2c5UqFHKECDphwTJR0LdZo1xaBQY8Mb8QDrt383WEewAiajxcHWraymGtsWxNWCviPaTFXIUTjV/1JACUCxCIs1/64GZ85Fs7GpBYxxFVuz3nHnjStOML12zeWob0WYmzNEGWefTP7ogjrjW2flCEm1Lo+250/FFc''4s6liFzJm+Czk7nfJHm/Ml7+A7Kvp+Wd2c5UqFHKECDphwTJR0LdZo1xaBQY8Mb8QDrt383WEewAiajxcHWraymGtsWxNWCviPaTFXIUTjV/1JACUCxCIs1/64GZ85Fs7GpBYxxFVuz3nHnjStOML12zeWob0WYmzNEGWefTP7ogjrjW2flCEm1Lo+250/FFce'头部加 原始字符串的.substr(3,1)值 尾部加.substr(7,1)'06546dae636aaccdb7a52c5c8065452b00000000000000aeaaae2b7a7de28e32ef37ae1427ee0c8f694609bddc4903b8e8fee50d783cc111757322046012LuyjJ'.substr(3,1) substr(3,1) 表示从索引3开始,提取长度为1的子字符串。
'4'
'06546dae636aaccdb7a52c5c8065452b00000000000000aeaaae2b7a7de28e32ef37ae1427ee0c8f694609bddc4903b8e8fee50d783cc111757322046012LuyjJ'.substr(7,1) substr(7,1) 表示从索引3开始,提取长度为1的子字符串。
'e'// 使用python实现