Docker 私有镜像仓库 Harbor 安装部署带签名认证
1. 准备工作
1.1 服务器信息
| IP | 主机名 | 内存(GB) | CPU核数 | 磁盘 | 操作系统 | CPU 架构 | Docker 版本 | 角色 |
|---|---|---|---|---|---|---|---|---|
| 10.0.0.13 | arc-pro-dc01 | 8 | 1 | 500GB | CentOS 7.9.2009 | x86_64 | docker 28.1.1 docker-compose v2.39.2 |
私有 Registry 服务端 |
| 10.0.0.14 | arc-pro-dc02 | 8 | 1 | 500GB | CentOS 7.9.2009 | x86_64 | docker 28.1.1 docker-compose v2.39.2 |
docker 客户端 |
必须:
- 给 Registry 服务端设置一个域名,比如 my.registry.com
- 客户端需要使用域名访问 Registry 服务端,所以要求每个客户端都可以识别服务端的域名
即在客户端和服务端的 /etc/hosts 文件中,存在:
10.0.0.13 arc-pro-dc01 my.registry.com
在使用浏览器访问私服的 Windows 电脑上修改:C:\Windows\System32\drivers\etc\hosts 文件,确保存在:
10.0.0.13 arc-pro-dc01 my.registry.com
参考以下文章完成虚拟机创建、虚拟机优化、集群基础配置以及 Docker 的安装部署:
- 使用 VMware Workstation 安装 CentOS-7 虚拟机
- 使用 Ansible 批量完成 CentOS 7 操作系统基础配置
- 使用 Ansible 批量安装 Docker
1.2 准备 harbor 离线安装包
下载地址:https://github.com/goharbor/harbor/releases/
文件:harbor-offline-installer-v2.13.2.tgz
上传到 arc-pro-dc01 服务器 /opt/app 目录下
1.3 准备 TLS 文件
在 arc-pro-dc01 服务器操作
$ sudo su -
$ cd /opt/app
$ ls
harbor-offline-installer-v2.13.2.tgz$ yum install ca-certificates -y
$ mkdir -p /etc/ssl/private
$ mkdir -p /usr/local/share/ca-certificates
$ openssl genrsa -out /etc/ssl/private/selfsignroot.key 4096# C (Country Name) 国家代码,使用 ISO 两位字母表示,例如:CN 中国 US 美国
# ST (State or Province Name) 州、省、自治区的名字,全称或缩写均可。例如:Guangdong、California
# L (Locality Name) 城市或地区名。例如:Shenzhen、Beijing
# O (Organization Name) 组织或公司名称。例如:Tencent、Alibaba、Example Corp
# OU (Organizational Unit Name) 组织单位(部门、分公司)。例如:IT Department、Security Team
# CN (Common Name) 常用名,通常填写【域名】或【个人名字】:$ openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=Beijing/L=Beijing/O=Personal/OU=Personal/CN=my.registry.com" \
-key /etc/ssl/private/selfsignroot.key \
-out /usr/local/share/ca-certificates/selfsignroot.crt$ openssl genrsa -out /etc/ssl/private/registry.key 4096# CN=arc-pro-dc01,服务器主机名
$ openssl req -sha512 -new \
-subj "/C=CN/ST=Beijing/L=Beijing/O=Personal/OU=Personal/CN=my.registry.com" \
-key /etc/ssl/private/registry.key \
-out registry.csr# 生成 openssl cnf 扩展文件
# 注意:DNS.1 = my.registry.com,一定要改成你自己的主机名
$ cat > certs.cnf << EOF
[req]
req_extensions = v3_req
distinguished_name = req_distinguished_name
[req_distinguished_name]
[v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = my.registry.com
EOF# 签发证书
$ openssl x509 -req -in registry.csr \
-CA /usr/local/share/ca-certificates/selfsignroot.crt \
-CAkey /etc/ssl/private/selfsignroot.key -CAcreateserial \
-out /etc/ssl/certs/registry.crt \
-days 3650 -extensions v3_req -extfile certs.cnf# 信任根证书
# ubuntu 系统执行
$ update-ca-certificates
# centos 系统执行
$ update-ca-trust
2. 部署
$ sudo su -
$ cd /opt/app
$ ls
certs.cnf harbor-offline-installer-v2.13.2.tgz registry.csr $ tar xf harbor-offline-installer-v2.13.2.tgz
$ cd harbor# 修改配置文件 harbor.yml(未列出的配置保持默认)
$ cp harbor.yml.tmpl harbor.yml
$ vim harbor.yml# 修改 hostname,修改为域名,而且一定是证书签发的域名
hostname: my.registry.com
# 修改 harbor_admin_password,访问密码
harbor_admin_password: 123456
https:port: 10443 # 默认 443,按需修改certificate: /etc/ssl/certs/registry.crt # 证书private_key: /etc/ssl/private/registry.key # 密钥
# 修改数据盘,默认是 /data
data_volume: /data/harbor# 执行脚本,下载镜像
$ ./prepare$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
goharbor/prepare v2.13.2 53905b30703f 6 weeks ago 208MB# 安装
$ ./install.sh...
✔ ----Harbor has been installed and started successfully.----# 服务文件
$ cat > /etc/systemd/system/harbor.service <<EOF
[Unit]
Description=Harbor
After=docker.service systemd-networkd.service systemd-resolved.service
Requires=docker.service
Documentation=http://github.com/vmware/harbor
[Service]
Type=simple
Restart=on-failure
RestartSec=5
ExecStart=/usr/bin/docker-compose -f /opt/app/harbor/docker-compose.yml up
ExecStop=/usr/bin/docker-compose -f /opt/app/harbor/docker-compose.yml down
[Install]
WantedBy=multi-user.target
EOF$ systemctl daemon-reload
$ systemctl enable harbor.service
Created symlink from /etc/systemd/system/multi-user.target.wants/harbor.service to /etc/systemd/system/harbor.service.# 清理安装包
$ cd ../
$ rm -f harbor-offline-installer-v2.13.2.tgz certs.cnf registry.csr
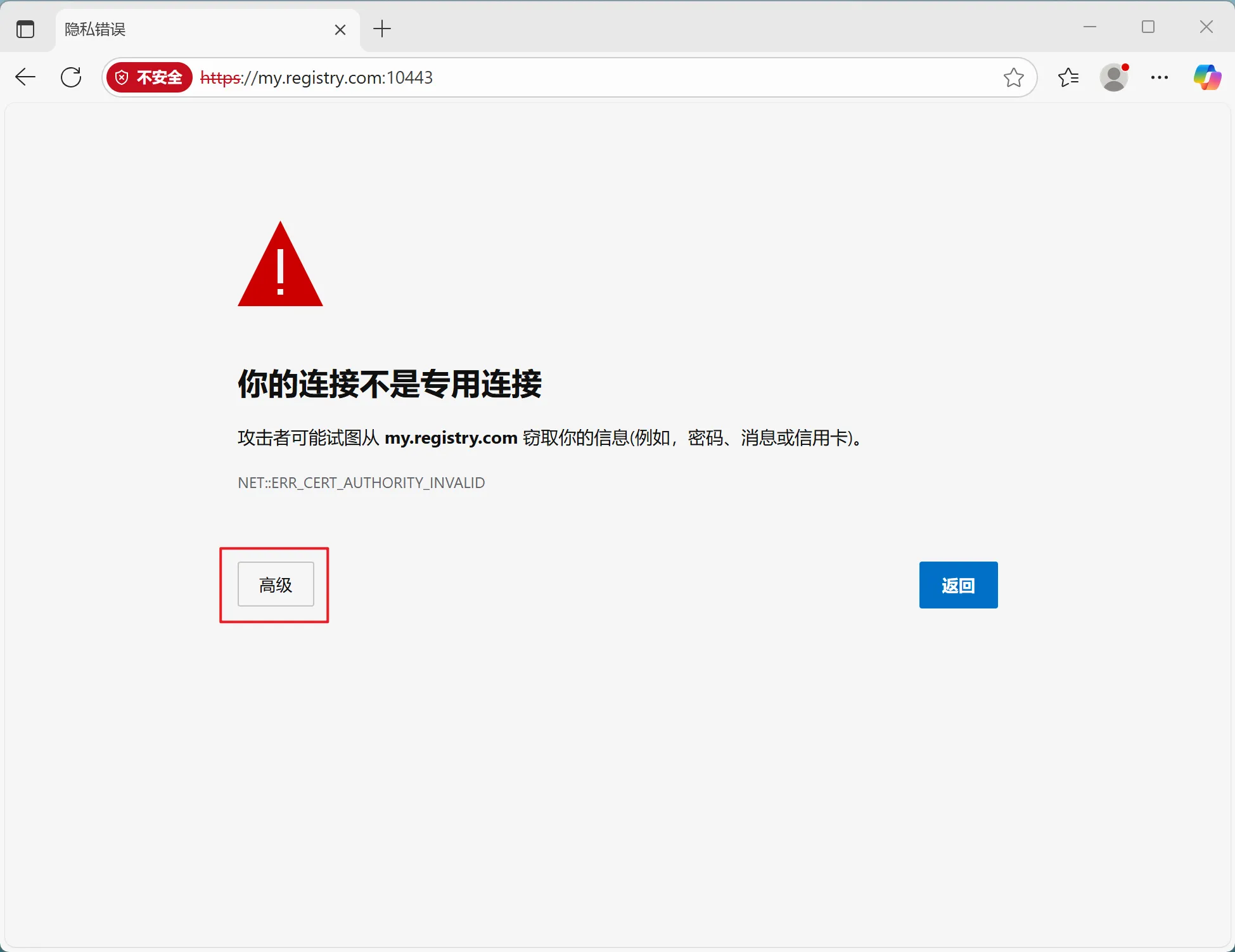
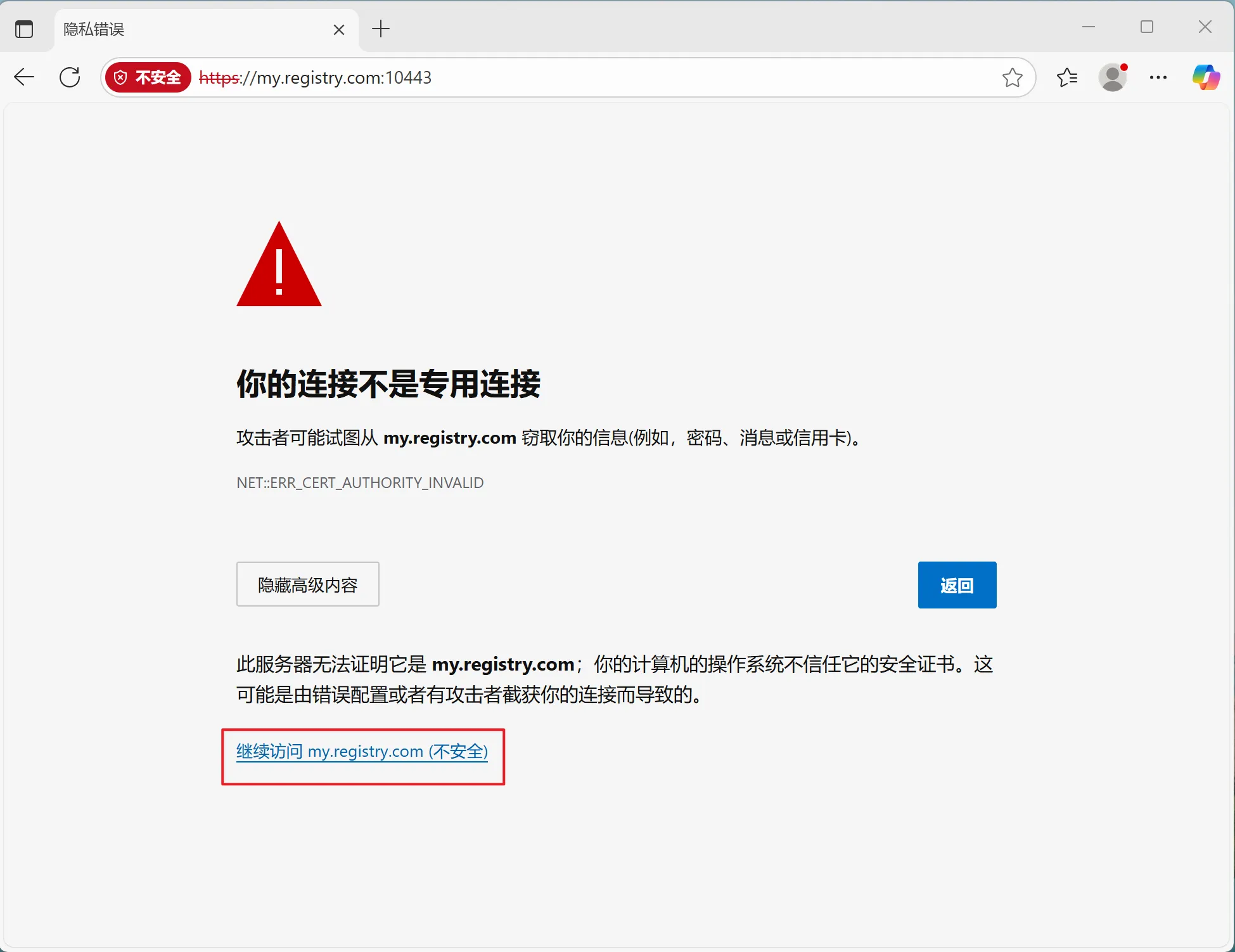
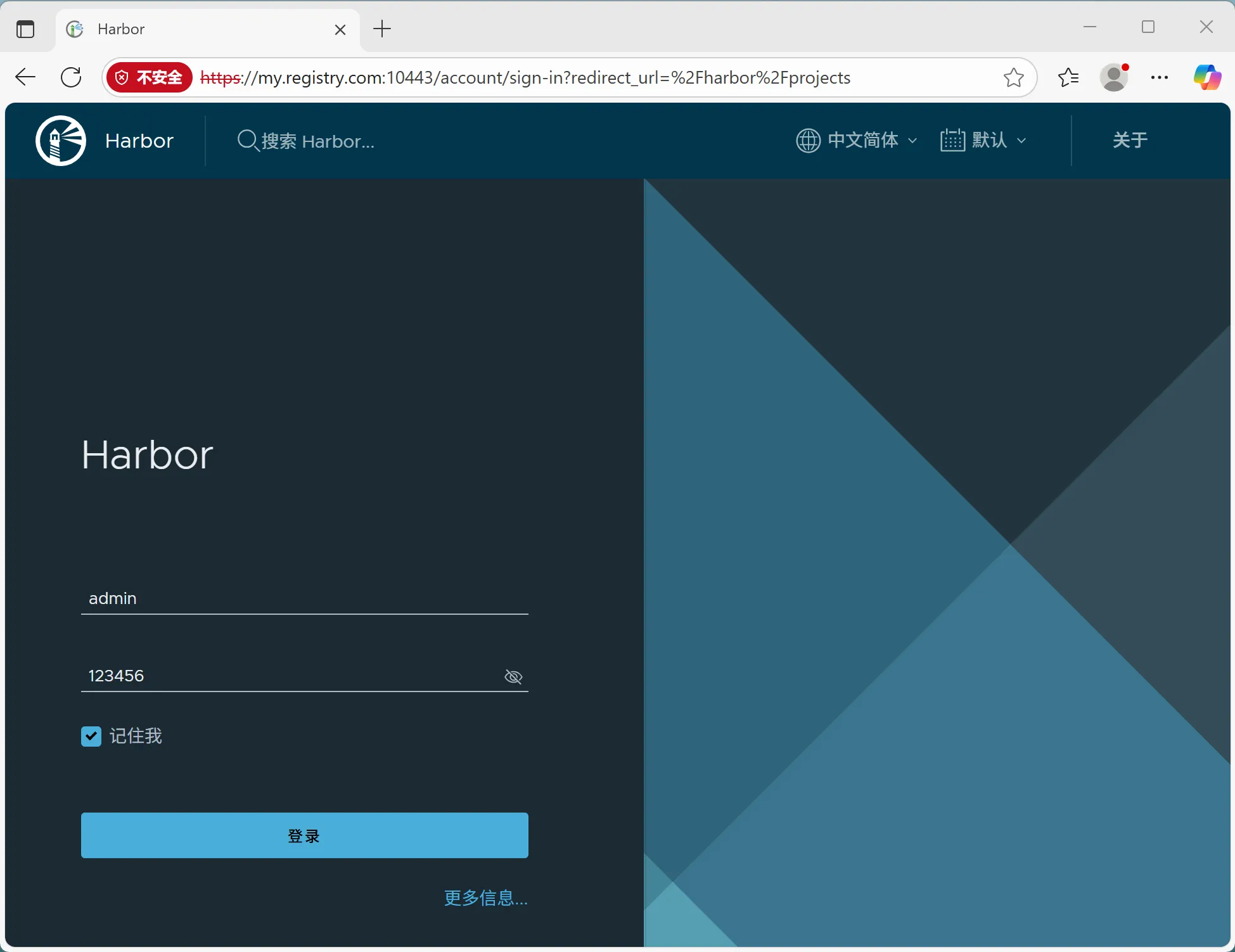

3. 客户端配置
arc-pro-dc02 服务器操作,使用 admin 用户操作
# 最后一级目录名一定是:私服域名:端口
$ sudo mkdir -p /etc/docker/certs.d/my.registry.com:10443
# 把服务端的 crt 文件拷贝给客户端
$ sudo scp my.registry.com:/etc/ssl/certs/registry.crt /etc/docker/certs.d/my.registry.com:10443/ca.crt# 设置服务端的账号密码
$ echo -n "admin:123456" | base64 # 输出 YWRtaW46MTIzNDU2$ mkdir -p ~/.docker$ tee ~/.docker/config.json > /dev/null <<-'EOF'
{"auths": {"my.registry.com:10443": {"auth": "YWRtaW46MTIzNDU2"}}
}
EOF# 如果没有配置 ~/.docker/config.json 文件,则在访问私有镜像仓库之前,要先登录
# 记录下登录私服的命令
$ docker login my.registry.com:10443 -u admin -p 123456
4. 测试
在 arc-pro-dc02 操作
$ docker pull nginx:1.29.1$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx 1.29.1 41f689c20910 4 weeks ago 192MB# 格式:域名:端口/项目名/镜像名/TAG
# harbor 默认的项目名是 library
$ docker tag nginx:1.29.1 my.registry.com:10443/library/nginx:1.29.1$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx 1.29.1 41f689c20910 4 weeks ago 192MB
my.registry.com:10443/library/nginx 1.29.1 41f689c20910 4 weeks ago 192MB# 推送
$ docker push my.registry.com:10443/library/nginx:1.29.1# 删除所有本地镜像
$ docker rmi my.registry.com:10443/library/nginx:1.29.1
$ docker rmi nginx:1.29.1
$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE# 拉取
$ docker pull my.registry.com:10443/library/nginx:1.29.1$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
my.registry.com:10443/library/nginx 1.29.1 41f689c20910 4 weeks ago 192MB
检查下仓库:

